Yesterday, Microsoft released a public public of some tools that Jeffrey Snover showed of at Microsoft Ignite last year, which was in essence basically just Server manager from within the Azure portal.
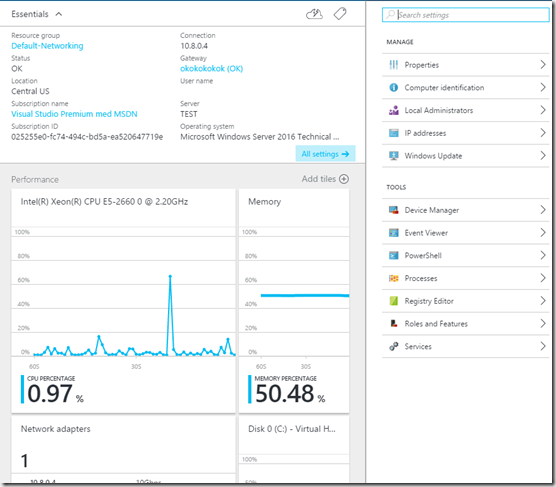
This tools is aimed for its first release to manage Windows Server 2016 servers, it can manage both Azure virtual machines and machines on-prem. So some of its capabilities:View and change system configuration
- View performance across various resources and manage processes and services
- Manage devices attached to the server
- View event logs
- View the list of installed roles and features
- Use a PowerShell console to manage and automate

Source: http://blogs.technet.com/b/nanoserver/archive/2016/02/09/server-management-tools-is-now-live.aspx
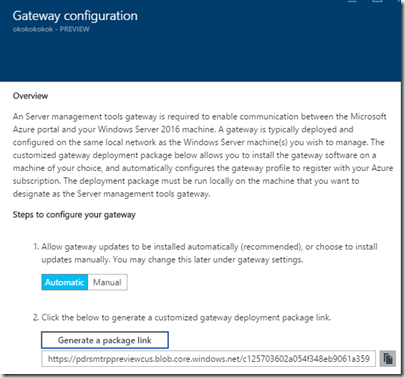
So what we do is that we deploy a Server Manager Gateway which we want to manage our virtual machines (Remember that the Server Gateway needs to have an internet connection)
NOTE: If you want to deploy the Gateway feature on 2012 server you need to have WMF 5 installed, which you can fetch here –> WMF 5.0: https://www.microsoft.com/en-us/download/details.aspx?id=48729
So when we want to deploy –> Go into Azure –> New –> Server Management Tools –> Marketplace 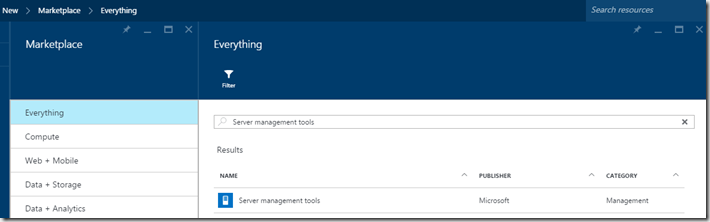
then we need to define the machine we want to connect to (Internal addresses, IPv4, IPv6 and FQDN)
So for the first run we need to create a gateway as well. If we want to add multiple servers that we want to manage we need to run this wizard again but then choose an existing gateway, for instance. 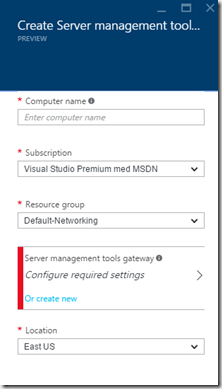
After we have created the instance we need to download the Gateway binaries and install on our enviroment
Then run the download from within the enviroment. Also important that if we want to manage non-domain based machines we need to run some parameters to add trusted hosts and such, as an example
winrm set winrm/config/client @{ TrustedHosts=”10.0.0.5″ }
REG ADD HKLMSOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystem /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1
NETSH advfirewall firewall add rule name=”WinRM 5985″ protocol=TCP dir=in localport=5985 action=allow (If you want specify firewall rules)
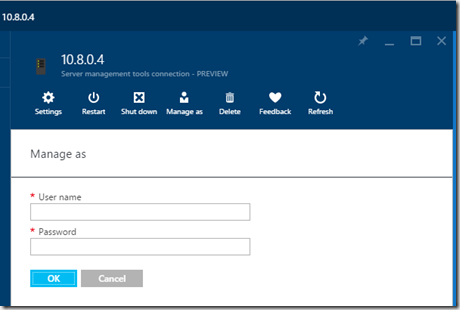
After you have installed the firewall rules. We need to specify credentials
After that is done we can now manage the machine from within Azure.