Today many organizations got faced with the issue that they have lost all access to their Microsoft apps, such as outlook/excel/word from their Windows machines. This is a bug caused by the latest signature updates from Microsoft (It comes with defender version 1.381.2140) and will impact machines that have ASR (Attack Surface Reduction Rules) that are configured to block “Block Win32 API calls from Office macro”
You can also see that status from Microsoft here, and that they are reverting the rule change.
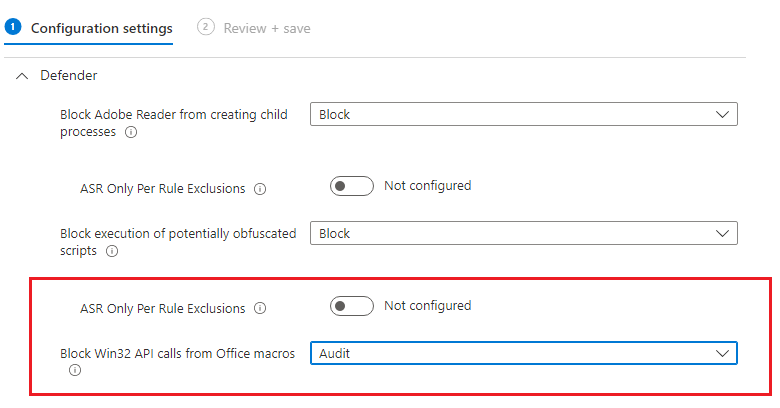
However, in the meantime, the fix is to configure the ASR rules in Audit Mode as seen in the screenshot here to audit mode instead of block.
When Microsoft uploads a new signature file, then this will no longer be needed, and you can set it back to Block mode…
The other issue is that the rule also deletes the Office desktop shortcuts, to fix this you can use the Office 365 quick repair.
- On the Windows Start screen, type Control Panel.
- Click or tap Control Panel.
- Under Programs, click or tap Uninstall a program.
- Click or tap Microsoft 365, and then click or tap Change.
- Click or tap QuickRepair, and then click or tap Repair.

Now since this is also deleting other shortcuts as well, I’ve made a kusto script to find the affected lnk files (Works if you have Microsoft Defender for Endpoint)
let deviceevent =
DeviceEvents | where ActionType == "AsrOfficeMacroWin32ApiCallsBlocked" and Timestamp >= datetime("2023-01-13 00:00:00Z") | order by Timestamp
| where FileName contains ".lnk"
| summarize count() by FileName, DeviceName;
DeviceInfo
| project LoggedOnUsers, DeviceName
| extend users = parse_json(LoggedOnUsers)
| mv-expand users
| extend loggedusers = users.UserName
| project DeviceName, loggedusers
| lookup kind = leftouter deviceevent on DeviceName
azuread/kqldetectasrblock at main · msandbu/azuread (github.com)