In many cases where you need an SSL certificate for your web servers (or other secure services like Lync, Exchange etc) you need to get a digital certificate from a third party certificate authority.
Now many third party CA’s will issue you with the CRT file and a CRT for the Certificate authority (Most Windows clients have most third party CA’s already in store (You can view them by opening mmc.exe and choosing certificates), and they also provide you with the RSA private key of the certificate in a separate file.
Now some CA’s also have the ability to let you download finished PFX files depending on what kind of service you need to deploy.
So check with the CA you are buying you’re certificates from that in most cases they have own certificates for web server and Lync, Exchange etc.
In Windows cases you need to merge these files into a PFX file.
Now before I tell you the secret I wish to explain what the difference is between the different files so you know how the certificate works.
- A
.csrfile is a certificate signing request which initiates your certificate request with a certificate provider and contains administrative information about your organization. - A
.keyfile is the private key used to encrypt your site’s SSL-enabled requests. .pemand.crtextensions are often used interchangeably and are both base64 ASCII encoded files. The technical difference is that.pemfiles contain both the certificate and key whereas a.crtfile only contains the certificate. In reality this distinction is often ignored.- The PFX extension is used on Windows servers for files containing both the public key files (your SSL certificate files, provided by for instance DigiCert) and the associated private key (generated by your server at the time the CSR was generated).
So in my case I had a crt file for the certificate itself and I had a crt file for the CA and I had the private key within a .key file.
Now I had to “merge” these into a PFX file so I could import it for use for Lync.
Now this is where openssl comes in.
Openssl comes often default with most linux distroes (ubuntu,fedora etc) in my case I had the Netscaler VPX available.
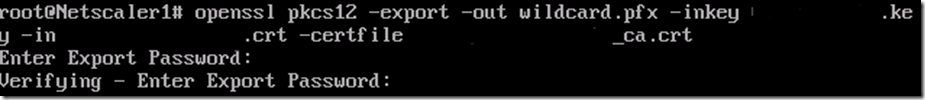
Before you can use openssl on Netscaler you have to type the command shell to enter the regular freebsd shell.
So type the command openssl pkcs12 –export –out certificate.pfx –inkey rsaprivate.key –in certificate.crt –certfile fileca.crt
After that you need to type a password to encrypt the pfx file.
Now after that is done you can copy the file from the share on either your unix share or Netscaler as in my case.
And you can try importing it in the certificate store.
Now when you import it you need to enter the password you used earlier in order to import it, and after you finished importing it open it and see that you have the private key available