In the last couple of years now, Microsoft has been working actively with new features in Azure Active Directory. For those who aren’t aware of what that is I can tell you briefly. It is identity as a service hosted in Azure (Its not the same as regular Active Directory even thou it shares the same name, but it is a user administration system and stores users in a catalog but it is built for the cloud. You also don’t have features like Group Policy and the notion of Machine objects are not present (well almost not) ill come back to that.
So when you set a Intune account, Office365 account or CRM online it will automatically create a Azure Active Directory tenant. All users that are created will be populated into that Azure AD tenant. From an administrator point-of-view all they will see is the users listed in their administration portal. In order to get full benefit of Azure Active Directory you need to go into Azure.
(Before I go into specifics you need to be aware of that there are 3 edtions of Azure Active Directory, free, basic and Premium) You can see the different features that are included in all 3 here –>
And also take note that Premium is also included in Microsoft EMS package (With Azure Rights Management and Intune) https://msdn.microsoft.com/en-us/library/azure/dn532272.aspx
So what do I mean that its built for the cloud ? well first of regular Active Directory which today is well established and one of the key important features of an on-premise setup does not work well with all the SaaS services that are being added to many enterprises today. Now many vendors include Active Directory integration in their Service (like Dropbox and such) but this is because that there are no native features in Active Directory.
Azure Active Directory on the other hand is built to be a platform which can include all the applications you want and work as an identity provider for all your SaaS applications or be on-premise. Now many are familiar with the syncronization tools that Microsoft offer to give a consistent user experience between on-prem and Office365. These tools will place users in Azure Active Directory tenant and will then allow us to build upon with new features and add integrations with other SaaS applications. We can also use Azure Active Directory standalone if we want a more pure cloud based setup.
So what does Azure Active Directory consist of ?
- Azure Access Control
- Azure Authentication System (SAML, OpenID & Oauth, WS-federation)
- Azure Graph
- Azure Rights Management Service
- Azure Multi-factor authentication
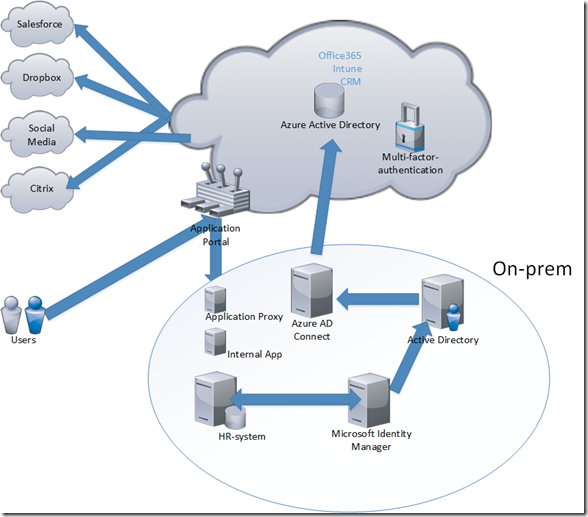
So all these services have a set of sub-features as well, but with all this Azure Active Directory can be a platform for managing identity across different clouds. So what might it look like ? Let’s think of a traditional enterprise where the HR application is where all new employees might be generated, the IT needs to setup a Active directory user and then he would need to provisiong access to all SaaS apps that the company uses.
What would it look like with Azure Active Directory setup with the different tools that Microsoft offers ?
Lets look at the example again, a new employee is setup in the HR system. Microsoft Identity Mnager(which is vNExt of Forefront) has a connector which allows it to grab hold of the information and has a workflow of how new employees should be setup and provisions a user in the local Active Directory. Azure AD Connect (Which is the new and upcoming Dirsync and AAD sync) will based upon the filters sync the user to Azure Active Directory. There can also be an ADFS which allows for true SSO since then ADFS will work as an SAML iDP and users can access it in real-time, another option is the setup user syncronization with password hash, this allows for users to use their username and passwords (a bit delayed when a password has been changed and a sync has not been run) but it does not give users a true SSO to services in Azure.
Now that the users are in Azure we can setup access to other SaaS services like SalesForce, Dropbox, other Social media applications and maybe even Citrix. Another option is to setup an internal application which we want to publish. This requires another feature called application proxy which will allow the users to authenticate users their Azure AD credentials (with or without MFA) then proxy a connection to a on-prem service)
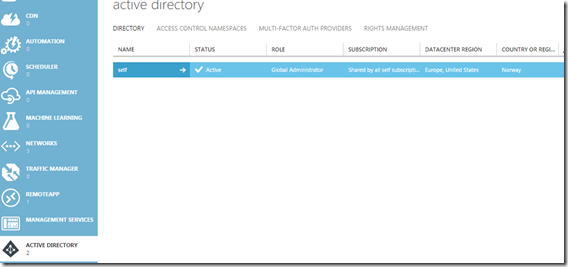
So far I’ve covered some of the basics. Lets look how it looks like. this is a screenshot from my management portal here I have one catalog
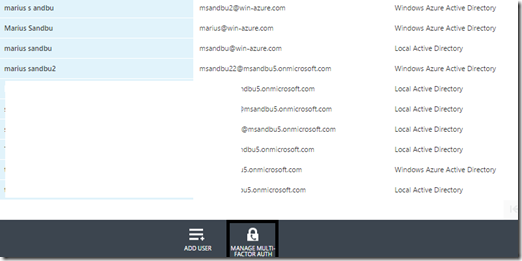
Inside here I have multiple users, some are cloud only and some are synced from on-premise. Here I also have option to manage MFA for my tenant ( I have a valid subscription)
Also inside the tenant catalog I have a bunch of different options which we are going to go trough.
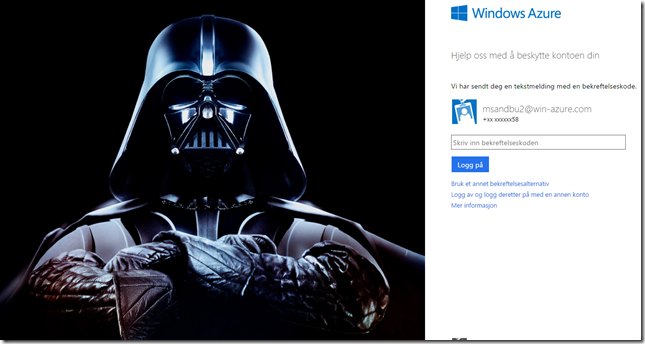
First of lets look at the configuration part. First of is the part to customize sign-in experience for our users.
So we can define background logo and background screen and such. Just basic stuff so when users try to login they might see this.
(Familiy photo!)
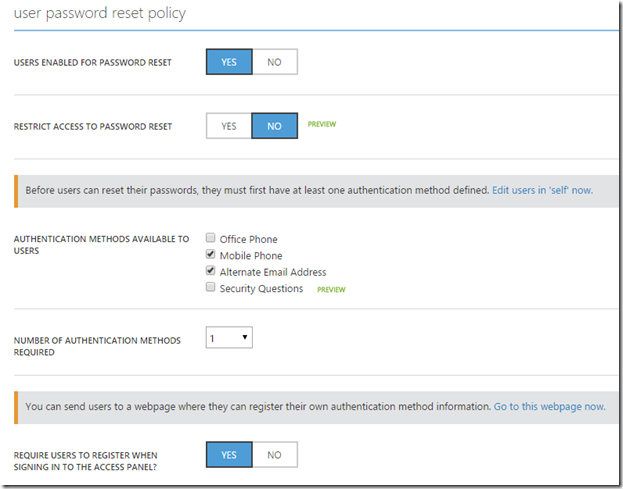
We also have configuration options for users password reset
We can also define a password write back feature (Which allows new passwords generated in Azure AD be written back to an on-premise Active Directory. Note that this requires Active Directory sync services be setup with write back feature.
As I mentioned earlier was that Azure AD has no idea about machine objects, well they kinda do. This is another preview feature but it allows for Windows 10 machines to “join” Azure Active Directory and allow for user login using their Azure AD credentials
(From a Window 10 tech preview machine)
After joining the Azure AD domain you can now sign it with your credentials
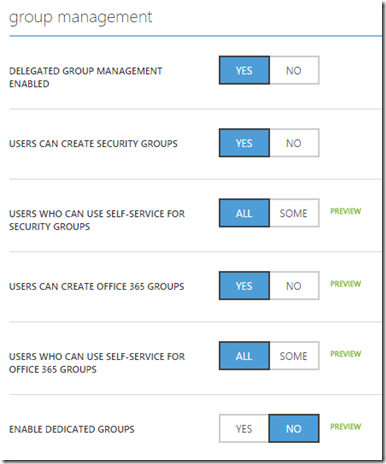
There are also alot of different options regarding Group Managment in Azure
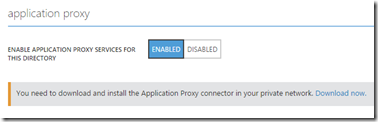
And one important part is Application Proxy
I have blogged about this before (https://msandbu.wordpress.com/2015/02/19/publishing-internal-applications-using-azure-active-directory-using-application-proxy/)
So let’s talk abit about the important part.. The Applications. Now Azure has some possibilities when adding applications. Work as an front-end authentication feature for instance on-prem applications. single-sign on for web based applications (password and federated SSO) and setting up MFA.
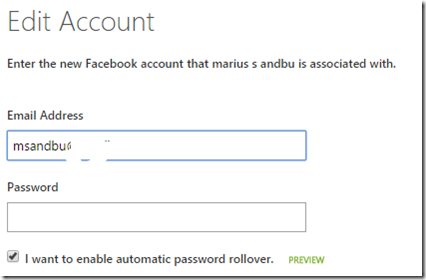
So let’s start with adding Facebook for our tenant and seting up the new feature called password roll-over (Which allows Azure AD to automatically update a password on behalf of the user)
So head on over to applications and choose add from Gallery
Find Facebook from the list and choose OK.
Click on Configure Single sign-on and choose Password SSO (Note that this requires that a user authenticate first with a username and password using a browser which has Azure AD extension installed. So when the user authenticated the extension will take the username and password, encrypt it and store it in the Azure AD tenant, so next time the users logs inn they don’t need to enter a username and password.
Then lets assign some users. Go into users and groups and find a users and choose Assign
Now we can also enter a username and password on behalf of the user
(Note that for Linkedin, Twitter and Facebook) we have the preview feature automatic password rollover)
Then click OK.
Now let’s add an on-prem application, now as I’ve blogged about it before it won’t show what the steps are but just to show what’s new.
For on-premise applications we can configure access rules, let’s for instance say that all users (except for sales users) need to use MFA when accessing this application outside of the Office.
Note that this is based upon IP whitelisting to allow who needs to access with or without MFA. Now this is part of the cloud based MFA feature, it is also possible to download a server component MFA which you can attach to your on-prem services as well using traditional AD https://msandbu.wordpress.com/2014/05/05/azure-multifactor-authentication-and-netscaler-aaa-vserver/
Now note that you can also use Azure Active Directory as an SAML iDP and use Graph API when developing other applications and setup integration with it. Now there are also some applications like Salesforce which offer full identity management
true SSO and provisioning.
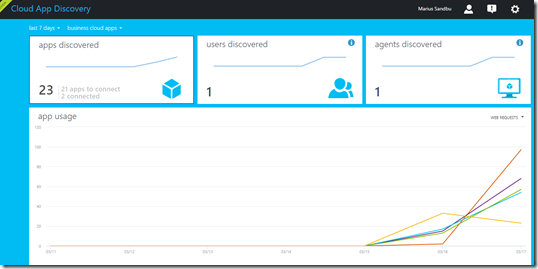
But this is only a few vendors which has added this support. Now if we are approaching a enterprise with “Hey you should get Azure AD, its great stuff!” and they have like 200 applications SaaS based which they use how can you get the overview ? Microsoft has also created something called Cloud App discovery (Which also is in preview –> https://appdiscovery.azure.com/)
Which is basically an agent that you download and run in your infrastructure it will gather info and find out what applications are being using and try to map them aganst those that Microsoft has support for.
So when you have setup the applications and given users access how does it look like ?
and voila user access!
Now this was just a brief touch into Azure Active Directory. In the last 6 months these features has been added to Azure AD
•Administrative units
•Dynamick Group membership
•Password roll-over
•Azure AD Connect Health
•Per-App MFA
•200+ applications in the gallery list
•Workplace join
•SaaS provisioning attributes
•MIM in Public Preview
•Azure AD Proxy
•Password write-back
•Azure AD on iOS and Android
•Conditional Access pr App
And this list will continue to grow, if you want to see what’s happning on Azure AD I suggest you follow Alex Simons (@Alex_a_simons) on twitter (He is the Product Manager for Azure AD, and from the looks of it from the feature list, he is feeding his developers Red Bull or something stronger)
and follow the Azure AD blog http://blogs.technet.com/b/ad/
Stay tuned for more news about Azure AD