Earlier today, Google published a article regaring how hackers can exploit a vulnerability in the SSL 3.0 protocol. Which you can read more about here –> http://googleonlinesecurity.blogspot.no/2014/10/this-poodle-bites-exploiting-ssl-30.html
You can also read more about the specific attack in detail here –> https://www.openssl.org/~bodo/ssl-poodle.pdf
Microsoft recommends that you disable SSL 3.0 using Group Policy on Windows Computer, since it is by default enabled, you can read more about it here –> https://technet.microsoft.com/en-us/library/security/3009008.aspx
UPDATE::: Citrix has added a article on this exploit as well –> http://support.citrix.com/article/CTX200238
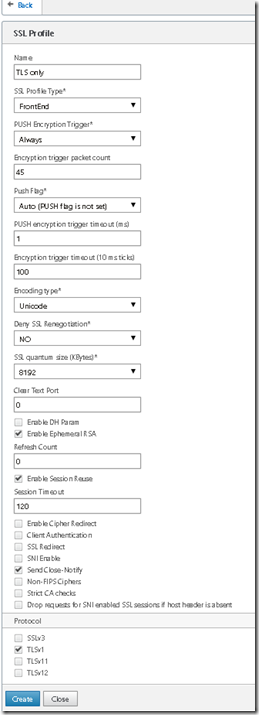
AND NOTE THAT IN THE SCREENSHOT DENY SSL RENEGOTIATION IS SET TO NO, THIS SHOULD BE PUT TO YES TO PROTECT AGAINST BEAST ATTACK.
Citrix Netscaler we can be fore flexible. For Netscaler Gateway we can define which type of SSL profiles or protocols which are going to be enabled for the session. We can create a new front-end SSL profile which we can attach to the Netscaler Gateway. Front end policies are used when a client is connecting to a vServer
Here I define that TLSv1 is enabled, and that the client cannot use SSLv3. (This is a screenshot from a VPX) and therefore TLSv1.1 and 1.2 cannot be enabled for this profile, and by default Citrix Receiver only supports TLS1 not the newer versions.
After I created the protocol I can bind it to a Gateway vServer
Now If I have other load balanced vServer I can also disable SSL for these vServers, but it is important to check if the clients that are connecting actually support TLS.
NOTE: I have not verified that this works for most browsers but I verified that my client can connect to the gateway vServer using TLS and not SSL3.