With 2012 R2 and RDS Microsoft has gotten better at devilering remote terminal server sessions. And since the cost of RDS is quite low compared to other platforms such as Vmware or Citrix.
RDS Gateway is a feature which allow us to tunnel RDP traffic inside HTTP packets or HTTPS to be exact and it can be used as an gateway to other servers, which makes it a suitble server to place in the DMZ.

Borrowed from technet: http://i.technet.microsoft.com/dynimg/IC470916.jpg
The problem with is that you do not have any high-availability functions on it, whcih makes it a bit hazzle to setup in a larger deployment. Sure we can use a farm but this is not a fully highly availble solution
With server 2012, Microsoft also added the use of UDP protocol to deliver the graphical while TCP is more used to maintain a session and control actions and such. It is also possible to disable UDP but you get a more sluggish experience.
Connection when UDP is enabled
So basically a RDS Gateway in 2012 R2 is a service which responds to TCP HTTPS (443) and UDP (3391)
Now how could this look like with a Netscaler in front, used to load balace between different RDS gateway servers ?
NOTE: This guide is going to assume that we are going to load balance 443 and 3391.
First we need to go into the Netscaler and add the different back-end servers which run the RDS gateway feature.
Next we need to attach a service to the back-end servers. Now since the RDS Gateway feature uses more then one port (and services in Netscaler is typically 1 Protocol 1 Port binding) we need to use the ANY protocol and we need to enther * in the port field. (We are going to use ACLs later to lock down the system) since this in general means that Netscaler will load balace any protocol and all ports.
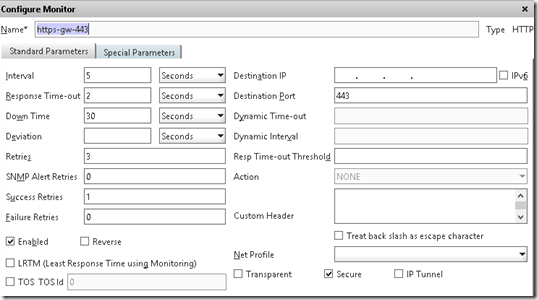
Now we can use a https monitor against the backend servers since https:443 is used to establish the connection. The problem is that since we entered * in the port field the built-in https monitor will fail since it does not know which port to prope. Therefore you should create a custom https monitor where you enter the specific port nr 443.
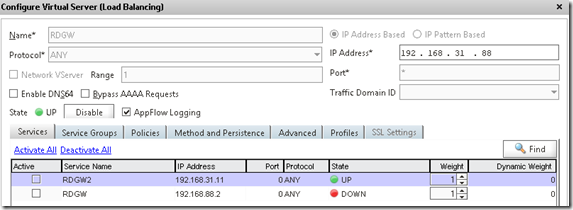
Which then again should be bound to the service. After you have created a service for each backend server (or service group) we need to create a load balanced service which is bound to Protocol ANY and Port ANY
Now the ANY protocol acts like a bridge so you do not need to put any certificates on this vServer but use it as an regular extension on the all-ready in place deployment ![]()
After you have created the service remember that you need to put ACLs in place for UDP 3391 and TCP 443 since the Netscaler will now by default load balance any requests to any back-end servers.
Also you should use persistency based upon how long you want the user to be able to use the same session on the gateway.