So Microsoft has been busy coming with numerous updates to Intune lately. The latest updates came last week, you can see updates here –> http://blogs.technet.com/b/microsoftintune/archive/2014/12/09/new-mobile-application-management-capabilities-coming-to-microsoft-intune-this-week.aspx
- Ability to restrict access to Exchange Online email based upon device enrollment and compliance policies
- Management of Office mobile apps (Word, Excel, PowerPoint) for iOS devices, including ability to restrict actions such as copy, cut, and paste outside of the managed app ecosystem
- Ability to extend application protection to existing line-of-business apps using the Intune App Wrapping Tool for iOS
- Managed Browser app for Android devices that controls actions that users can perform, including allow/deny access to specific websites. Managed Browser app for iOS devices currently pending store approval
- PDF Viewer, AV Player, and Image Viewer apps for Android devices that help users securely view corporate content
- Bulk enrollment of iOS devices using Apple Configurator
- Ability to create configuration files using Apple Configurator and import these files into Intune to set custom iOS policies
- Lockdown of Windows Phone 8.1 devices with Assigned Access mode using OMA-URI settings
- Ability to set additional policies on Windows Phone 8.1 devices using OMA-URI settings
Now one of the cool features is the managed browser app. This allow us to manage how content is opened and displayed from this app. By default the application can do two things.
- Allow the managed browser to open only the URLs listed below – Specify a list of URLs that the managed browser can open.
- Block the managed browser from opening the URLs listed below – Specify a list of URLs that the managed browser will be blocked from opening.
So we define a URL which a user can open (NOTE: You can see what kind of policy prefix I can use here –> http://technet.microsoft.com/en-us/library/dn878029.aspx#BKMK_URLs)
The application itself is available from Google Play https://play.google.com/store/apps/details?id=com.microsoft.intune.managedbrowser but in order to use it in conjuction with Intune policies we need to deploy the application from Intune itself. Besides the managed browser application, Microsoft also released some other applications like Intune PDF viewer, Intune AV player, Intune Image player which users can download from google play. So when a user uses the managed browser, opens a PDF link from the managed browser, it will automatically open in the Intune PDF viewer (Where we can define settings like cannot copy/paste screenshot etc.
So when we setup this we need to deploy the package to our users, so they can install it from the company portal. NOTE: Dont deploy it right away we need to create some policies first.
So when setting up policies we have a lot of new policy features we can define for our devices.
Now the Managed Browser Policy is just the allow/deny list. And we have the mobile application management policy, here we can define how the apps are going to integrate and what users can do when the content is displayed.
When we are done creating the policies, we can deploy these policies. Now unlike other policies these need to be deployed as a part of the software and not directly to users or groups. So when setting up the browser deployment we can add the policies.
Now we can head on over to the mobile device! First of I need to sync my mobile device policy
Then I install the managed browser app and other compents I need from the company portal
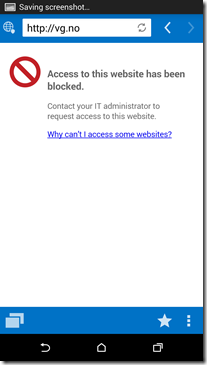
Now I am ready to use managed browser. When I open a URL that is on the deny list I get this error message.
When I open a URL that is on the allow it works like a regular browser, but when I download a PDF file you can see there is a loading bar underneath the URL this is because the managed browser downloads the PDF internally in the App and then
we are switched over to the Intune PDF viewer
so again, alot of new stuff arriving to Intune, looking forward to the next chapter