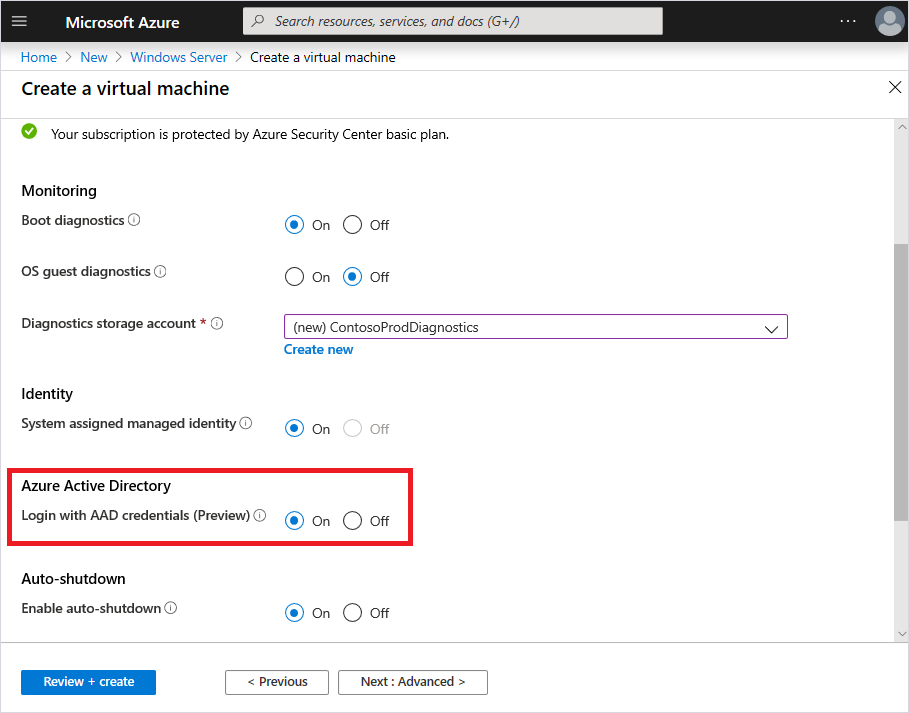
An announcement that came out last week, was that we now have the ability to use our Azure AD Credentials to login to a Windows Server based VM running in Azure. Previosly this has only been available for Linux based VM’s running in Azure but also Windows 10. A Big news is also that Microsoft is looking into supporting this for non Azure VMs too sometime next year.
You can see the official announcement here –> https://techcommunity.microsoft.com/t5/Azure-Active-Directory-Identity/Azure-AD-authentication-to-Windows-VMs-in-Azure-now-in-public/ba-p/827840
Utilizing Azure AD based login for Windows Server in Azure it allows for the use of
- Utilizing the same federated or managed Azure AD credentials you normally use.
- No longer having to manage local administrator accounts.
- Using Azure RBAC to grant the appropriate access to VMs based on need and remove it when it is no longer needed.
- Requiring AD Conditional Access to enforce additional requirements such as:
- Multi-factor authentication (MFA)
- Sign-in risk using Azure Active Direcetory Identity Protection
- Automating and scaling Azure AD join for Azure based Windows VMs (This can be automatically installed using Extensions)
Still since Azure AD does not give any NTLM/LDAP support for applications that still require LDAP or Active Directory. In order to get this capability you would need to have Windows Server 2019 Datacenter edition or Windows 10 1809 with a custom extension enabled, this is done by choosing “login with AAD Credentials” when creating a new virtual machine. It should also be noted that you can have a Server AD joined and Azure AD joined at the same time .
Or installing the custom VM extension
az vm extension set \ --publisher Microsoft.Azure.ActiveDirectory \ --name AADLoginForWindows \ --resource-group myResourceGroup \ --vm-name myVM
To allow a user to log in to the VM over RDP, you must assign either the Virtual Machine Administrator Login or Virtual Machine User Login role. An Azure user with the Owner or Contributor roles assigned for a VM do not automatically have privileges to log in to the VM over RDP. This is to provide audited separation between the set of people who control virtual machines versus the set of people who can access virtual machines.
You can also see that the devices are registered in Azure AD by looking for them under devices.

Conditional Access
Now to apply Conditional Access policy, you must select “Azure Windows VM Sign-In” but an important aspect is that this also then you must supply multi-factor authentication claim as part of the client that initiates the RDP session to the target Windows VM in Azure. The only way to achieve this on a Windows 10 client is to use Windows Hello for Business PIN or biometric authenication with the RDP client. Support for biometric authentication was added to the RDP client in Windows 10 version 1809. Remote desktop using Windows Hello for Business authentication is only available for deployments that use cert trust model and currently not available for key trust model. You can see more about the feature here –> https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10-version-1809#remote-desktop-with-biometrics

Troubleshooting
1: You can find the AAD logs under Applications and Services Logs –> Microsoft –> Windows –> AAD –> Operational in Event Viewer which will show any issues with the use of the service. In addition which you need to be aware of is that from the initiated machine you need to have a machine is joined to the same Azure AD either direct joined or hybrid Azure AD joined.
You will also get access from the VM when you are trying to connect if it is Azure AD joined.

NOTE: That this feature does not work with Azure Bastion since that is a mechanisms with does proxy interaction between the client and the server you are connecting to. Also this feature does not work with B2B or Azure Lighthouse which means that you need to have a native users within the tenant if you want to leverage this authentication method.