Yesterday Microsoft released an update for CVE-2020-1350, a Critical Remote Code Execution (RCE) vulnerability in Windows DNS Server that is classified as a ‘wormable’ vulnerability and has a CVSS base score of 10.0. This issue results from a flaw in Microsoft’s DNS server role implementation and affects all Windows Server versions (not the DNS Client, and also domain controllers which have DNS are also affected)
This vulnerability was discovered by security researchers at Checkpoint dubbed SIGRed (You can see all the technical details here –> https://research.checkpoint.com/2020/resolving-your-way-into-domain-admin-exploiting-a-17-year-old-bug-in-windows-dns-servers/ ) essentially it is how DNS Servers handles TCP payload response over a certain size result bigger than 65,535 bytes.
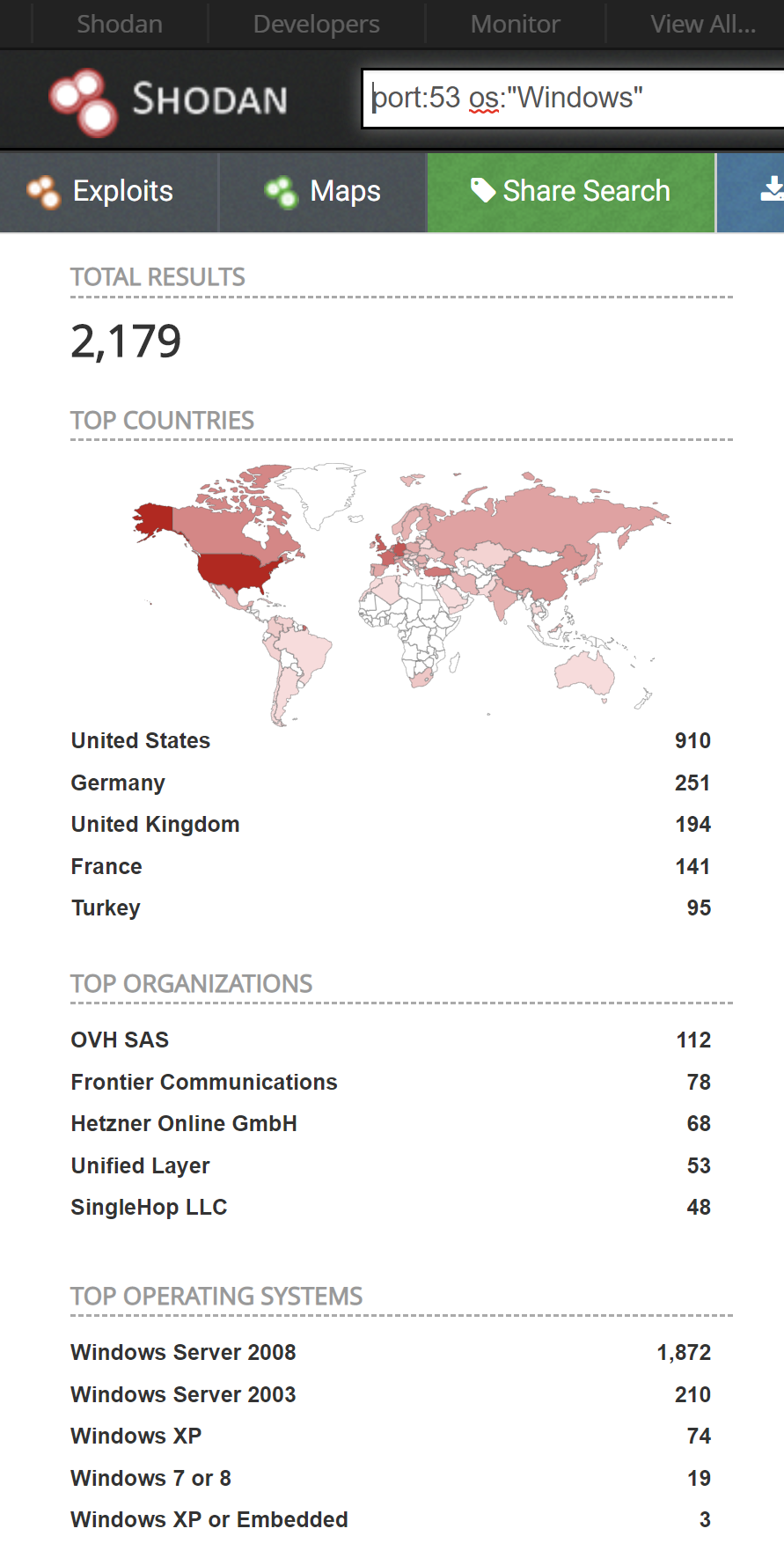
So just how bad is it? Just one email away

Microsoft has already released a fix for this vulnerability, which you can find here –> https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350
NOTE: The Patch requires a server restart, and the registry workaround under requires just a service restart.
As a temporary workaround, until the patch is applied, you can change setting the maximum length of a DNS message (over TCP) to 0xFF00, which should eliminate the vulnerability. You can do so by executing the following commands:
reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters” /v “TcpReceivePacketSize” /t REG_DWORD /d 0xFF00 /f
net stop DNS && net start DNS
You can use the following PowerShell script to check if your server is vulnerable https://github.com/T13nn3s/CVE-2020-1350
Or if you have Log Analytics / Sentinel running you can also use Kusto Query.
Update | where KBID == “4565511” or KBID == “4558998”
or KBID == “4565483” or KBID == “4565503” | distinct Computer, Product, KBID
How many are affected? Many are using the combination of DNS and AD and secondly there are a lot of servers running Windows DNS publically available. However CVE–2020-1350 does not require a direct connection to port 53. If you phish someone, they click on the domain, and their Windows DNS server receives a recursive query response, it is owned.
Just a quick FAQ for those questions that are coming in.
Does it affect domain controllers? As long as the domain controllers are running DNS role which most are, they are affected by this bug.
Which versions of Windows Server are affected? All versions of Windows Server from Windows Server 2008 – to the latest 2019 edition.
Does it require that the DNS server is public? No, essentially an attacker can setup a malicious domain, send an email to a end-user which clicks on a link which in turn will get the DNS server to do a name lookup to that malicious domain which can then compromise the DNS server