Following up on the previous AzureStack blogpost (Software load balancing –> http://msandbu.org/azurestack-breakdown-of-load-balancing-component/) I wanted to continue on the firewall component, which is also a new component which is now part of Windows Server 2016 as well. The solution in place in AzureStack is the same one that is available in Azure aka (Network Security Groups) now compared to regular firewalls, the NSG can also be based on pure later 2 network, meaning that we can specify rules on virtual machines on the same subnet.
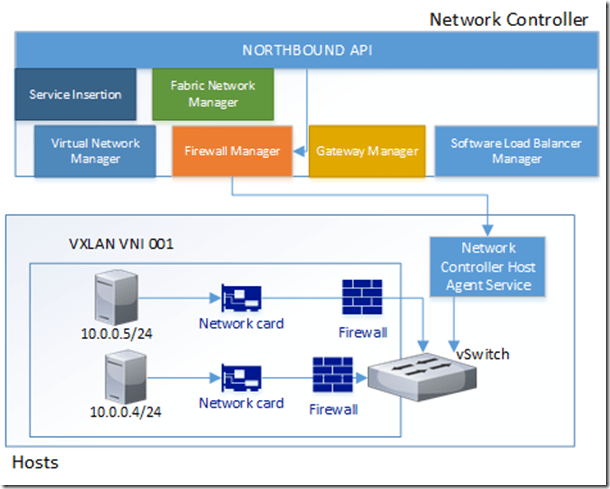
So again using the distributed firewall the central component here is the Network Controller, which is used to deploy and manage the policies across the different hosts. All Hyper-V host has a Network Controller Host agent service installed, which is used as a component for multiple services but for the distributed firewall it is a vSwitch port host agent running.
So all the ACLs are configured in each vSwitch port, independent of the actual host running the virtual machine, but ACL’s can also be associated to subnets as well. Since all the Hyper-V hosts in AzureStack have this component installed, and the rules apply regardless of where the virtual machine is located. So for instance if we have multiple hosts, the same rules will apply since the Network Controll Host agent service is quering the Network controller to get the central policy for a partciular virtual machine.
So all traffic will be inspected before they actually leave the switch, actually it is inspected on that particular port before the switch forwards the traffic to the destionation. The ACL’s that can be specified are 5 tuple on both directions, and all ACLs are applied regardless of what kind of operating system is running in the guest virtual machine.