So as of today, Azure Active Directory Premium is available in trial for all users. For those that aren’t aware of what Azure Active Directory Premium is in short Identity and Access Management for the cloud so its a extension of the previous features which include,
* custom domains
* users and groups
* directory integration with local Active Directory
* MFA (which I have blogged about previously http://bit.ly/1lkQ0NO)
The premium part allows for single-sign and multi-factor authentication to any cloud application. To show the entire functionality.
Active Directory Premium edition is a paid offering of Azure AD and includes the following features:
- Company branding – To make the end user experience even better, you can add your company logo and color schemes to your organization’s Sign In and Access Panel pages. Once you’ve added your logo, you also have the option to add localized versions of the logo for different languages and locales. For more information, see Add company branding to your Sign In and Access Panel pages.
- Group-based application access – Use groups to provision users and assign user access in bulk to over 1800 SaaS applications. These groups can either be created solely in the cloud or you can leverage existing groups that have been synced in from your on-premises Active Directory. For more information, see Assign access for a group to a SaaS application.
- Self-service password reset – Azure has always provided self-service password reset for directory administrators. With Azure AD Premium, you can now further reduce helpdesk calls whenever your users forget their password by giving all users in your directory the capability to reset their password using the same sign in experience they have for Office 365. For more information, seeSelf-service password reset for users.
- Self-service group management – Azure AD Premium simplifies day-to-day administration of groups by enabling users to create groups, request access to other groups, delegate group ownership so others can approve requests and maintain their group’s memberships. For more information, see Self-service group management for users.
- Advanced security reports and alerts – Monitor and protect access to your cloud applications by viewing detailed logs showing more advanced anomalies and inconsistent access pattern reports. Advanced reports are machine learning-based and can help you gain new insights to improve access security and respond to potential threats. For more information, see View your access and usage reports.
- Multi-Factor Authentication – Multi-Factor Authentication is now included with Premium and can help you to secure access to on-premises applications (VPN, RADIUS, etc.), Azure, Microsoft Online Services like Office 365 and Dynamics CRM Online, and over 1200 Non-MS Cloud services preintegrated with Azure AD. Simply enable Multi-Factor Authentication for Azure AD identities, and users will be prompted to set up additional verification the next time they sign in. For more information, see Adding Multi-Factor Authentication to Azure Active Directory.
- Forefront Identity Manager (FIM) – Premium comes with the option to grant rights to use a FIM server (and CALs) in your on-premises network to support any combination of Hybrid Identity solutions. This is a great option if you have a variation of on-premises directories and databases that you want to sync directly to Azure AD. There is no limit on the number of FIM servers you can use, however, FIM CALs are granted based on the allocation of an Azure AD premium user license. For more information, see Deploy FIM 2010 R2.
- Enterprise SLA of 99.9% – We guarantee at least 99.9% availability of the Azure Active Directory Premium service. For more information, see Active Directory Premium SLA
- More features coming soon – The following premium features are currently in public preview and will be added soon:
- Password reset with write-back to on-premises directories
- Azure AD Sync bi-directional synchronization
- Azure AD Application Proxy
Now in order to activate premium in your azure account you need to have an existing directory service in place, then you can go into the directory and then create a premium trial
Then you have to activate the trial.
After premium is enabled you have to license users to use the feature. In the trial we are given 100 licenses which we can use.
But note that now we have other panes here as well that we can use to configure the single-sign on experience. Now in an ideal scenario we would have a Active Directory catalog synced and with a public domain which is verified, i’m in vacation mode so therefore im going to show how to use a cloud only user and setup SSO to different cloud applications.
If we go into users we can see all the users which are located in the cloud directory, either they are synced from a local AD or they are a Microsoft account.
So we have some users in place, if we go into Configure pane we have the option to customize the access page which users are using to use SSO to web applications. We also have the option to enable users to do password reset (NOTE: that this requires that users have either a phone or alternative email adress defined) this can also me combined with password write back to on-premises AD. http://msdn.microsoft.com/en-us/library/azure/dn688249.aspx
Now we want to add some SaaS applications for the test, go into applications and choose add.
There are 3 ways to add an application. Either add a an regular web application or a native client application, choosing a application from the gallery (which atm consists of over 1000 different SaaS applications. Or if we want to publish an internal application outside of our network (this uses Microsoft Azure AD Application Proxy)
So in our case we are going to choose applicaiton from the gallery. Now I have already added some applications to the list here, and some appliactions have different capabilities then others. For instance Salesforce application has the capabilities for provisioning users automatically after a dirsync for instance, while twitter or Yammer do not have this capability.
There are also two types of SSO for each applications, we can either use ADFS (federation based SSO) or use Password based SSO.
Important to note that password based SSO is when a user click on a application from the access portal and has a plug-in installed which then populates the username and password field of the application when entering, it also has some requirements.
Configuring password-based single sign-on enables the users in your organization to be automatically signed in to a third-party SaaS application by Windows Azure AD using the user account information from the third-party SaaS application. When you enable this feature, Windows Azure AD collects and securely stores the user account information and the related password.
Password-based SSO relies on a browser extension to securely retrieve the application and user specific information from Windows Azure AD and apply it to the service. Most third-party SaaS applications that are supported by Windows Azure AD support this feature.
For password-based SSO, the end user’s browsers can be:
- IE 8, IE9 and IE10 on Windows 7 or later
- Chrome on Windows 7 or later or MacOS X or later
Now if I again go back to the application list and click on an application I have usually two options. Defining SSO options and choosing who has access.
NOTE: for salesforce I have the ability to configure automatic user provisioning as well.
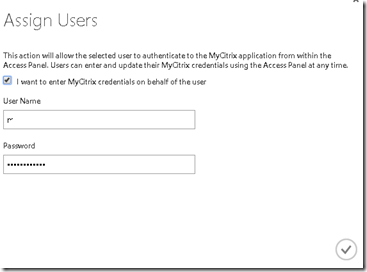
Now go into assign users and choose an user in the directory. Now when using password based SSO you get the option of entereting the credentials on behaf of the users (now they are also able to enter this information on the access portal)
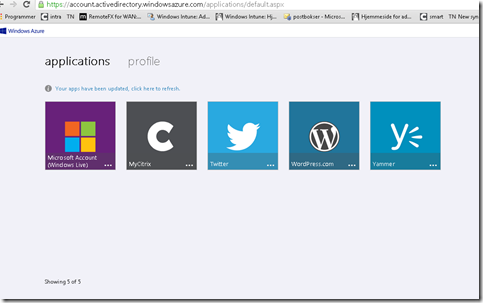
After this is done and you have assigned users to different applications they can open the access portal (which can be found here –> http://myapps.microsoft.com ) After I login here with my username I am able to SSO to the application I click on from the portal (NOTE that this requires a browser plug-in installed) Microsoft has also already created an wiki containing best-practices for accessing SSO applications.
And voila, I have my personal little password manager. From a user perspective I have the option to change credentials from this portal I can also change my password for my main user (which is a outlook user in this scenario) But this is a huge step in how to manage access to users and applications with a little touch of the cloud.









Pingback: Certificação Azure - Implementing Microsoft Azure Infrastructure Solutions Exam 70-533 - Lucas Chies