This is something I have been meaning to try out for a while, since the preview release at Ignite. Advanced Threat Analytics is a new software from Microsoft (which comes from a purchace Microsoft did a while back) but it focuses on some of the more common problems with security in Windows enviroment, such as Golden tickets, Pass the hash, abnormal user behavior and so on.
Now Microsoft ATA is pretty simple architecture it consist of two components and a MongoDB base where the data is stores, the two components
The ATA Center performs the following functions:
-
Manages ATA Gateway configuration settings
-
Receives data from ATA Gateways
-
Detects suspicious activities and behavioral machine learning engines
-
Supports multiple ATA Gateways
-
Runs the ATA Management console
-
Optional: The ATA Center can be configured to send emails or send events to your Security Information and Event Management (SIEM) system when a suspicious activity is detected.
The ATA Gateway performs the following functions:
-
Captures and inspects domain controller network traffic via port mirroring
-
Receive events from SIEM or Syslog server
-
Retrieves data about users and computers from the domain
-
Performs resolution of network entities (users and computers)
-
Transfers relevant data to the ATA Center
-
Monitors multiple domain controllers from a single ATA Gateway
These roles can be deployed on two different virtual machines or on the same VM, really important that during setup of the ATA center, define that communcation happen using the external IP on Center communication and management IP. By default it sits on 127.0.0.2 then you need to install both components on the same server.

Now the Gateway needs to be able to see the DC (or Global Catalogs) traffic using Port Mirroring, which can either be used in a physical enviroment with SPAN or RPSAN, or we cna setup port mirroring in a virtualized fashion.
I have my demo enviroment running on Hyper-V which allows me to easily setup Port mirroring. First thing I need to do is configure the NIC on my DC to do port mirroring.
Then I need to add another NIC on my Gateway VM and configure that as a destination mirroring mode.
I also need to enable the NDIS monitoring filter on the vSwitch
Before the initial setup note that there are some limitations in the preview…
Make sure that KB2919355 has been installed!
Only enter domain controllers from the domain that is being monitored. If you enter a domain controller from another domain, this will cause database corruption and you will need to redeploy the ATA Center and Gateways from scratch!
After you have deployed both components, all you need to do is define the domain controller and NIC, in the management console.
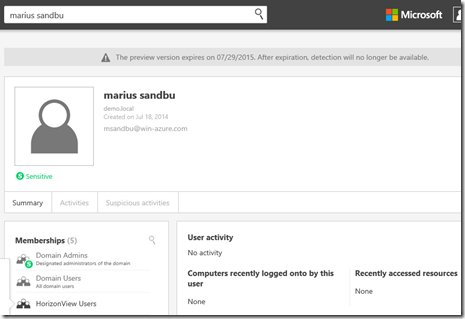
Now after this is done we can verify that it has connectivity by checking the dashboard and search for a user
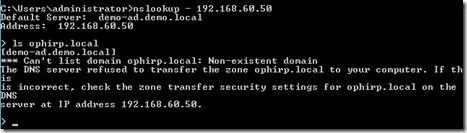
Now by default ATA takes about 2 weeks before it can etasblish a baseline for how regular activity works, but it has some default alters which we can trigger to make sure that it works as it should. For instance we can use a DNS reconnasince attack
Simple nslookup and ls paramter. This will then trigger in the console
Since this is still preview it has a some limitations, as of right now it cannot detect PtH, so stay tuned for more about this when the full release comes.