The last couple of days I’ve seen a lot of traffic on my blog regarding the posts on Netscaler ( And I don’t have so many of them!) And with the recent events regarding Cisco ACE and Microsoft Forefront TMG, I’m guessing that a lot of people are looking into the option to switch over to Citrix.
Cisco has always been huge in the networking market, but in the ADC (Application Delivery Controller) market they have never gotten the huge market share that they were hoping for, therefore a couple of weeks ago they decided to stop further development of their ACE product. And in similar events Microsoft decided to stop further development on their TMG product. TMG is not the same product like Netscaler/ACE/BIG-IP thou it has a lot of the same functions and features.
So back to Netscaler what can it offer:
* Advanced load balancing
* Content and app caching
* Database load balancing
* Application Firewall
* Secure Remote Access
* Advanced server offload
* Application acceleration
* Integration with Citrix
* Access Gateway features
* Web interface
* Scale up and Scale Out features
You can read more about the different features here –>
http://www.citrix.com/products/netscaler-application-delivery-controller/features.html
Now the Netscaler product comes in 3 Different versions.
MPX: Which is the hardware appliance, is again split up into different models,
http://www.citrix.com/products/netscaler-application-delivery-controller/features/platforms/mpx.html
As you can see most of the models here have a “pay-as-you-grow” options, so for instance if you buy a MPX 7500 and your company is growing and you need more throughput you can upgrade your 7500 to a 9500. So it’s the same hardware as before you just “unlock” more features.
You can see all the different models and features here –> http://www.citrix.com/content/dam/citrix/en_us/documents/products/netscalerdatasheetaugust2012.pdf
VPX: Is a software based virtual appliance, which is available for Hyper-V, VMware and XenServer.
http://www.citrix.com/products/netscaler-application-delivery-controller/features/platforms/vpx.html
Here as well you have a “pay-as-you-grow” solution so you can upgrade it if you need more throughput, the downside to using a VPX is that it does not have hardware based SSL acceleration (which the MPX has), which allows for a lot less SSL connections.
SDX: Is the best of both worlds. It is a hardware appliance like the MPX but in also has capabilities of running VPX. So it’s a piece of hardware which basically runs a stripped down XenServer which allows to run multiple VPX inside. And since this piece of hardware has SSL acceleration capabilities it does not have downside of a regular VPX. It allows for up to 40 VPX’s and that will allow for true multi-tenancy.
You also have the “pay-as-you-grow” option here.
http://www.citrix.com/products/netscaler-application-delivery-controller/features/platforms/sdx.html
Also Netscaler comes in 3 Different editions (Like most of Citrix products)
You can see the different editions and their limitations in this datasheet
http://www.citrix.com/content/dam/citrix/en_us/documents/products/netscalerdatasheetaugust2012.pdf
A summary,
Standard = Use for Load-balancing (Web and DB) also has Citrix Web interface and TCP optimization
Enterprise = For more advanced features – cloud bridge, edgesight for netscaler, branch repeater client.
Platinum = Includes all the features.
So what do I need for my organization ?
Well first of you need to figure out what your needs are.
1: Do I need just the load balancing for my Web-servers?
2: SSL VPN solution and/or SSL offloading?
3: Advanced Web load-balancing and caching and optimization?
4: Multi-tenancy solution ?
5: DDos defenses ? Or do I have a firewall in front which is fully capable ?
6: Just for my Citrix pieces (Access Gateway and Web interface)?
7: SQL load-balancing?
8: How many users do I have?
You also need to calculate the bandwidth usage the service you are going to load-balance, most of the products (for instance Lync) has well documented traffic usage for each feature.
Let’s take an example if I am a small business that just needs to load-balance my 2 webservers for my internal users (and I have 100 of them) the smallest VPX would suffice.
If I am a enterprise service provider and I offer fully multitenancy solution where customers can setup LB for all their services I would recommend a SDX (The best solution regarding version is to start with the lowest system you think you need and upgrade when you need to grow)
So after you have chosen the model (remember that you always need two of them, since if you only have 1 you have a single point of failure). The next part is setting up the device.
Remember that a Netscaler operating system consists of two parts.
1: Part is FreeBSD (The Appliance uses this part for booting and for logging)
2: Part is the core os (NSOS NetscalerOS) Which controls the traffic in / out of the appliance.
When a appliance boots, it will get system image from the flash and decompress and put it into the ram. The config file is also fetched from the flash and put into the ram. (Which is know as the running-config)
(You can show the running-config from CLI by running the command, show ns runningconfig if you want to see the saved config you can run the command show ns.conf )
You can access it either via a console (serial cable or console via the hypervisor )
And remember that you can save at anytime by running the command save ns config, if you screwed up you can restart the Netscaler (if you didn’t save your config)
But when you start the NS appliance the first thing you see is that it asks for an IP (Which is known as the NSIP Netscaler IP) Which is used for management purposes and clustering. You also enter a subnet mask and a gateway.
After that you can save and quit the config menu and you can now access the appliance via a webconsole. You can also see more info regarding the interface by running the command show ns ip 10.0.0.2
As you can see here it says that “Management Access is enabled” and FTP, Telnet, SSH and GUI is enabled.
So we should disable the insecure access methods before we continue. By running the commands set ns ip 10.0.0.2 –telnet disabled and same for FTP
And there are other things we should configure as well, change the default password for the user “nsroot”
You can do this by running the command config system user nsroot PASSWORD (something very very safe)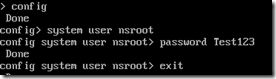
Also you SHOULD enable NTP sync with a authorized ntp server.
add ntp server IP –minpool integer –maxpool integer
enable ntp sync
Now we can log onto the Web GUI. (Im using version 10 of the Netscaler VPX you can get a free trial for your hypervisor from citrix.com and might add that the web gui is much improved in V10)
The default username and password for the local system user on a netscaler is nsroot and nsroot
So after you have logged in you will come to main menu.
Its split up into 3 panes (Dashboard, Configuration and Reporting) and what you see here is the configuration pane.
If I go to the Dashboard, you see a lot of read-time information regarding well.. everything you want to see
I can choose if I wish to view SSL connections, TCP handshakes, HTTP traffic etc..
The reporting pane is just that, you can create reports and there are a bunch out of the box that we can view as well.
But most of the time we are going to be in the configuration pane.
Now what other things do we need to do in order to load balance a service?
First of we have to design how the netscaler should be placed in our infrastructure, most of the designs are based on
one-arm-mode or two-armed-mode.
In one-arm-mode the netscaler has ONE interface, and on that interface external traffic comes in and the inside traffic out on the same interface (traffic is split by using VLAN’s)
In two-arm-mode the netscaler has TWO interfaces, 1 for external traffic comes in and comes out and 1 for internal traffic. So this is the much more common deployment.
Now in both scenarios the traffic to the back-end servers are flowing as the following.

Now when the client connects to the web service as the virtual IP (90.90.90.90) The Netscaler (depending on the LB rules) make a connection to one of the servers which are connected to that virtual service with the Netscaler SNIP(Subnet IP)
The Subnet IP is an address that connects the netscaler to the servers in the backend, so you should have an SNIP address for each subnet you want to have services in.
So SOURCE IP —> VIRTUAL IP (NS) SNIP —-> WEB SERVER 10.0.0.4 (BASED ON LB) so for the web servers it will appear that the connections come from the same IP. And the same will go back to the clients
WEB SERVER –> SNIP (NS) VIRTUAL IP —> SOURCE IP, so for the clients all they see is that one IP address which may house loads of web servers.
Now is there a problem with this ?
Well yeah.. if you have a web server you probably want to have logging in place for the IP address of the client, now you have the Netscaler option which known as use “Source IP mode”(USIP) which will allow for clients to do a direct connection with the backend servers. But what is the downfall of this ?
1: TCP Multiplexing which allows for the netscaler appliance to have one connection to the webserver will be disabled when you use Source IP mode.
2: When backend servers see the source IP they will look at their default routing table instead of returning the traffic to the netscaler, so therefore the servers with go with the local gateway instead of the netscaler. When the backend servers try to connect to a TCP connection with the client, the client will drop connection since it is awaiting its response from the Netscaler VIP.
So in the case you use Source IP mode you need to set the default GW on the backend servers to point to the NS.
You can set USIP mode in modes.
Configuration –> Settings –> Configure Modes –> Use Source IP
Alternative enable ns mode usip
In case of logging we have another choice( inject HTTP header option which allows the Netscaler to inject the source IP header into the http request which again allows logs on the webserver to contain the IP-address of the client. )
But in general I would recommend that you don’t use USIP.
Now lets setup a load-balancing configuration.
Before we continue remember that you need to setup at least 3 addresses on the NetScaler
1: NSIP
2: VIP
3: SNIP or MIP
There are a few things we need to find out before we can setup LB, what kind of service to we need to load-balance and what servers are hosting this service. And we need to setup a monitor towards that service as well, this monitor check is the service in the backend is responding on that server, if one server is not responding for a particular service it is taken out of the LB queue. So we need.
1: Servers (The list of servers that have a particular service running
2: Service (What kind of service is it ? Webhosting port 80?
3: Monitors (Checks if the service on the server is responding if not it is taken out of the LB-queue until it start responding again)
4: Virtual IP (a virtual IP address which the Netscaler will respond to)
All this is added together and it creates a load balanced service on a virtual Ip address which consists of the servers in the server list.
So lets go ahead and create a LB service. First we add a VIP and a SNIP
Go to configuration pane –> IPs and add a IP address. Remember that a VIP is the ip address that the end users are going to connect to, the SNIP is a ip which the netscaler uses to connect to the servers in the backend.
After that go to the load-balancing pane further down below.
Go to servers and add the servers that has a service.
(Remember that this is just a list of servers, you don’t define the services here)
After that go to monitors –>
As you can see the HTTP monitor is enabled by default
This does a HTTP HEAD command, and if it is working as it should you should get a code 200 response.
You can see this by opening the http monitor 
After that we add the service,
We add a service that runs on port 80 on one server and add the HTTP monitor. (Remember to add this for both servers) And have a very descript full name each service on each server.)
Now that we have both services on both servers it should look like this
(In my case I don’t have any hosts on these IP addresses yet so therefore they are stated as Down) because the monitor is trying to do http request on them.
Now at alas we will add the virtual server that will point to the http server on these 2 servers in the backend. Go to Load balancing and virtual server –>
Remember to add both of the services on those servers (If you wish to load balance differently for instance it you have a more power on one of the server you can alter the weight on that server to 2, then this server will take twice the load)
You can also go to method and persistence to change how the service is load balanced. By default it is set to “least connection” that server with least connections will get the next connection, this will happen until they are even. You can also specify persistence (This will define if a client should talk with the same server it spoke with earlier) the most typical choice here is cookie insert for web services. But we will leave it at the default.
Now I’ve added a HTTP server with actually responds to HTTP 
You can see that is responds to http request if I open a browser to IP 10.0.0.26
And if you are like me and would like to do it via the CLI you can do this.
Run the command add service servername ip http portname
Next we need to add the services to a virtual IP. (that will do the load balancing )
first we do a add lb vs servicename http ip 80
then we bind the services to that virtual ip
bind lb vs servicename serviceserver
After that you can do a
sh lb vs v1 to show that if the load balancing is active
Phuh! long post, next one will be regarding setting up a cluster on Netscaler, since you would always need 2 x Netscalers so you don’t have a single point of failure. And we are going to integrate authentication with LDAP.
Now I would also recommend that some user look at the command reference sheet from Citrix eDocs
http://support.citrix.com/servlet/KbServlet/download/20679-102-665857/NS-CommandReference-Guide.pdf









Very good. Weee.. 😀
EV