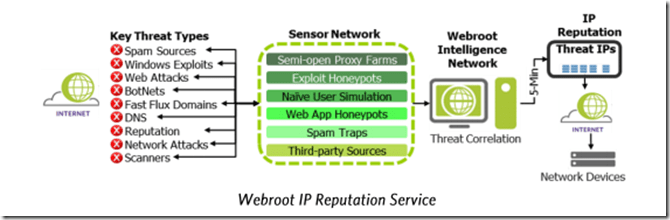
NetScaler IP Reputation which is a pretty new feature and is as of now only included as part of Platinum, is one of the few Cloud Based Services that Citrix has included in NetScaler so far. Now IP Reputation is a pretty simple yet effective means to get updated list of “known bad IP addresses” which for instance are part of a botnet, known for network atttacks, scanners and so on. The IP reputation feature from Citrix is leveraging the IP reputation feature from another company called WebRoot, which specialized in gathering all these bad IP addresses from their sensor networking and creating their IP reputation database, which in return the NetScaler downloads and can reference in policies.
NOTE in order to enable and make IP reputation work you should make sure that To the NetScaler appliance should be able to connect to api.bcss.brightcloud.com on port 443. When we enable the IP reputation feature NetScaler will download a copy of the database and place it in the /var/nslog/iprep/ folder on the appliance.
You can monitor the updates to the database by using this command cat /var/log/iprep.log, note: When the reputation feature is enabled, the NetScaler Webroot database is downloaded. After that, it is updated every 5 minutes.
This will list out if if done any updates or changes to the database. So now that we have a database containing all the different bad IP addresses how can we reference them in the NetScaler? There are multiple ways we can do so, we can either reference them in an application firewall policy or use it in a responder policy for instance (Responder consumes alot less CPU processing then application firewall and in most cases you just want to drop traffic from known malicious IP addresses, but the expression syntax is the same)
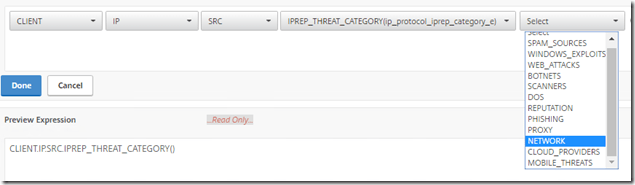
So for instance we can create a responder policy that looks like this:
Which basically says that if there is a client IP that is mapped to an IP address in the Webroot DB that NetScaler has, the responder policy is going to drop the traffic, so now we just need to bind this policy to a vServer. Now the ip addresses contained in the list is also categories so we can specify more detailed on WHAT kind of IP segment we want to block in the DB, for instance if IP-addressses known for bad reputation, known spam sources and so on.
Now in the upcoming blog post we are going to look more on how we can use IP reputation to do in-depth inspection in HTTP headers to find known malicious IP addresses as well.