With NetScaler build 11.65, Citrix introduces Security Insight as part of the Insight Appliance. This feature is used to give real-time insight into attacks, and recommendations on countermeasures.
NOTE: Security Insight requires Application Firewall enabled, since it reports based upon AppFw violations and rules. You also need the same version of Insight and the NetScaler appliance for this to be supported and for it to work.
To setup Security Insight there are basically three steps.
1: Setup NetScaler Insight build 11.65 and NetScaler appliance with the same build number, then add the NetScaler appliance to Insight
2: Alter the AppFlow paramters on the NetScaler appliance to send Security Insight data
set appflow param -SecurityInsightRecordInterval 60 -SecurityInsightTraffic ENABLED
This enables it to send the IPFIX templates and data to Insight.
3: Enable Application Firewall rules and bind it either globally or to a particular virtual server. The simplest way to setup it could be done like this.
add appfw profile pr_appfw -defaults advanced
set appfw profile pr_appfw -startURLaction log stats learn
add appfw policy pr_appfw_pol “HTTP.REQ.HEADER(“Host”).EXISTS”pr_appfw
bind appfw global pr_appfw_pol 1
This enabled the StartURL feature on the Application Firewall modul, which is set to learn which will learn the start URL on a virtual server, if someone tries to go into the virtual server on another start url for instance http://test.fqdn.no/test2.html they will be violating the StartURL rule and will then trigger an alert.
This will then generate an AppFlow alert which will be sent to Insight Center and processed there.
So in my case I have a simple virtual server, which represents a HTTP server. (This could also be Exchange, SharePoint, eCommerce sites for instance)
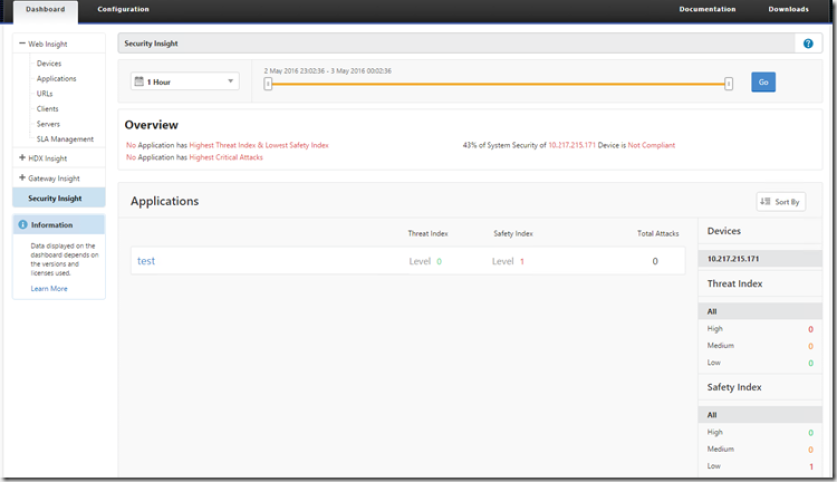
After the configuration is done, you will see when logging into Insight and going into –> Security Insight that a device with Security Insight AppFlow will appear in the list
As of now I only have one Application called “test” which has an Application firewall policy attached to it.
NOTE: Yeah I love descriptive application names.
So after triggering some Appfw violations by accessing the virtual server on another URL which is not the start URL I get a bit more information. It will get some more information about my Application Firewall policy and NetScaler System security policies, ill come back to that in a bit.
When clickcing on the virtual server form within Insight I get more information about what is configured for the virtual server in terms of AppFw signatures and security checks and so on. Also a threat level is generated based upon the violations that are created, te hmore critical the attacks on an application, the higher the threat index for that application. Values range from 1 through 7.
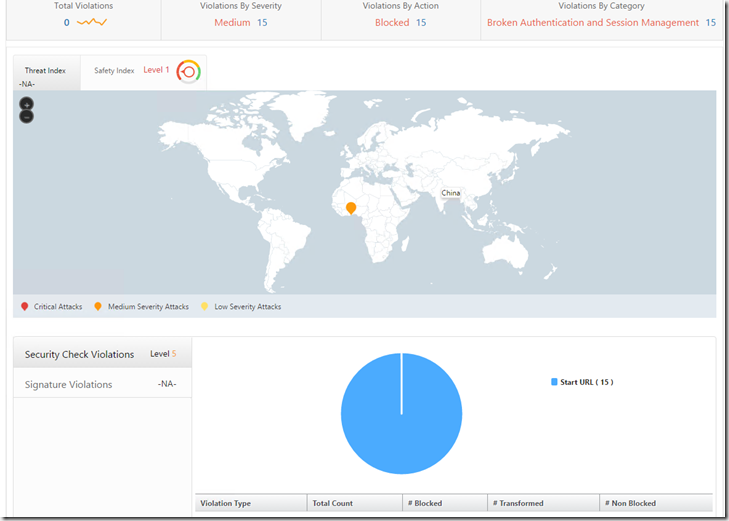
So if I click on the threat index I get a detailed overview of what kinds of violations that has been triggered.
I can also from here click on the violation type and get information about client ip address, and if I have GeoIP database added it will draw a map of where it originated from
Now what we saw from the earlier pane, we noticed that my Application Firewall configuration was level one and that my NetScaler System Security was level 3, which means that Insight noticied that I haven’t done any changes beside the default and I should take a closer look at the system configuration to harden it more..
So if I now go into the NetScaler system policy configuration I get feedback on what I should do, to ensure that the NetScaler is more locked down
The NetScaler System Security is built up of different categories.
- Access
- Monitoring
- Logging
- Cryptography
- Others
The different categories still show limited information and the crpytography pane just looks at if SSL/TLS is enabled and if it is using AES256 as the default encrpytion.
So what’s missing?
Even thou this is a good starting point, I would love for Citrix to go even deeper here in this feature, because so many have no clue about how secure their external services are. So some things I would love to see in the product moving forward
- Cipher groups indexing
- Certificates indexing
- HSTS enabled?
- DDoS attacks?
- AAA bruteforcing ?
Would love for them to incorporate features from what ssllabs are running and display a better SSL/TLS overview of each virtual servce.
And also all the recommendations that are shown from Insight should be able to configure directly from Insight, instead of just show what you should do and then you need to log into the appliance and then configure it from there.