UPDATE 2: Patches now released from Microsoft CVE-2021-34527 – Security Update Guide – Microsoft – Windows Print Spooler Remote Code Execution Vulnerability (Still missing some operating system) CVE updated to announce that Microsoft is releasing an update for several versions of Window to address this vulnerability. Updates are not yet available for Windows 10 version 1607, Windows Server 2016, or Windows Server 2012. Security updates for these versions of Windows will be released soon. Other information has been updated as well. This information will be updated when more information or updates are available.
MORE Info –> PrintNightmare CVE-2021-34527 – Patches | Marius Sandbu (msandbu.org)
There is a new high severity vulnerability dubbed Print Nightmare, which exploits a vulnerability in the Print Spooler service. This vulnerability can provide full domain access to a domain controller under a System context. To be able to use this exploit it requires that you authenticate as a domain user. You can see a short video of the exploit here https://lnkd.in/dgqEjwN
The vulnerability itself is possible because, The Microsoft Windows Print Spooler service fails to restrict access to the RpcAddPrinterDriverEx() function, which can allow a remote authenticated attacker to execute arbitrary code with SYSTEM privileges on a vulnerable system.
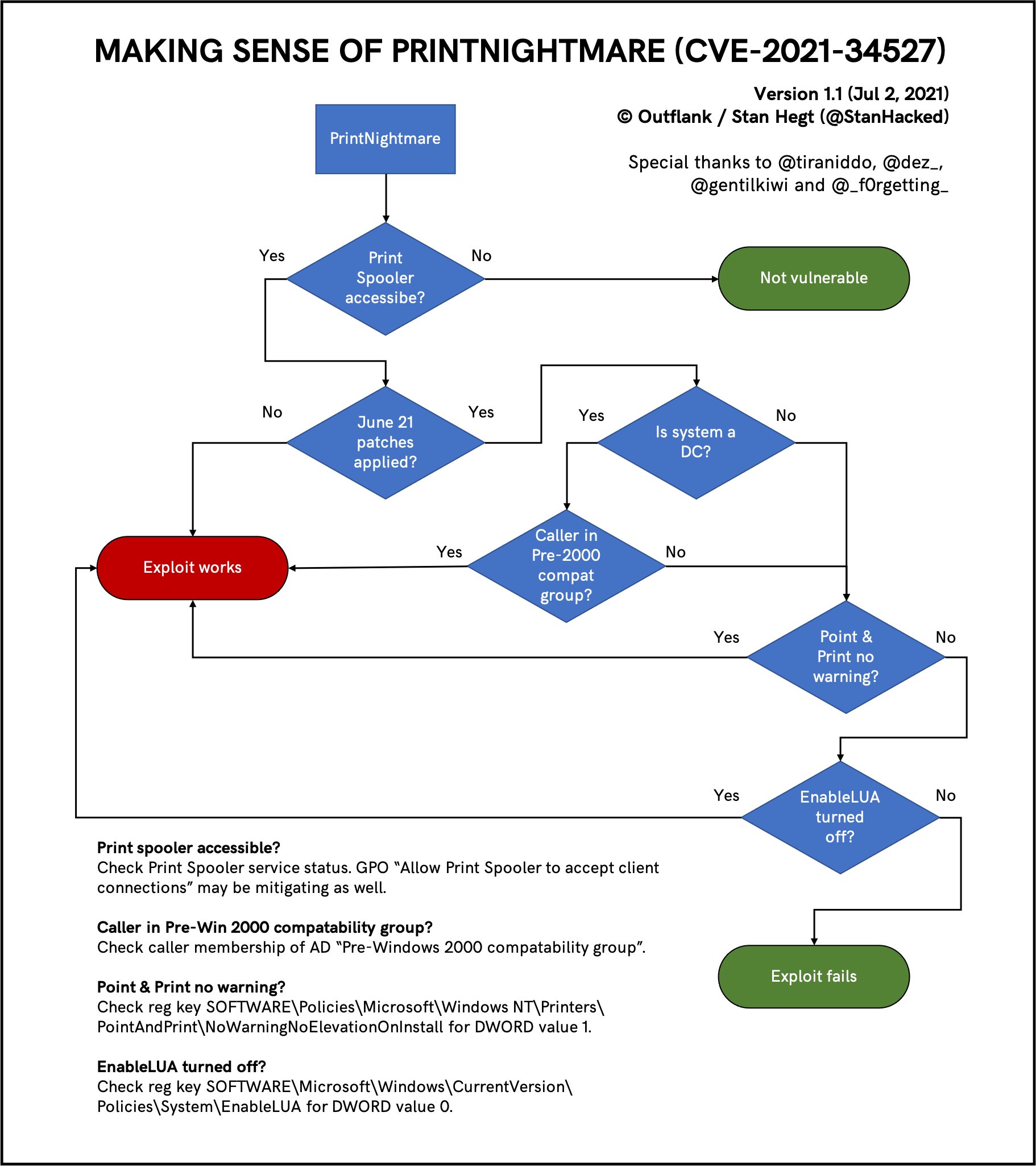
Flowchart of the vulnerability (Source: (1) Stan Hegt (@StanHacked) / Twitter
It should be not be confused with CVE-2021-1675. PrintNightmare is not the same not the same as CVE-2021-1675, which was fixed in the patch in June, there is currently no patch available for PrintNightmare. You can read a writeup of the former CVE here –> Exploit on Windows 10, or escalation of privileges “made in Poland” – Cybersecurity – Blog AFINE Cyber Academy
There will also be more information from US CERT on the subject here as well –> PrintNightmare, Critical Windows Print Spooler Vulnerability | CISA
It should be noted that there are still no known sources of any ransomware, worms, or others that are actively using this vulnerability yet.
This applies to all Windows Server versions (from Windows Server 2008 – 2019, including Windows 10) you can see the latest PoC here –>
There are already multiple PoC available on GitHub which provides information on how to use it, example –> afwu/PrintNightmare (github.com).
Here is also a PowerShell PoC for local privilege escalation calebstewart/CVE-2021-1675: Pure PowerShell implementation of CVE-2021-1675 Print Spooler Local Privilege Escalation (PrintNightmare) (github.com)
It should be noted that most endpoints will be safe from this attack with the built-in Windows Firewall default rules

However, the critical part is for Print Servers / Domain Controller and other servers with a LOCAL privilege escalation such as Citrix / VMware or other terminal services. Where often print is much used.
For all systems where the print spooler service is not required (it is enabled by default) remember to disable the service, preferably update with the latest patches https://lnkd.in/d8mGsb2 (NB: Still sources are stating that the patch does not fix the issue) so please do both)
For Print Servers you can use the following workaround Fix for PrintNightmare CVE-2021-1675 exploit to keep your Print Servers running while a patch is not available – TRUESEC Blog
The print spooler service can be done using CLI/PowerShell
CLI: net stop spooler
PowerShell: Stop-Service -Name Spooler -Force Set-Service -Name Spooler -StartupType Disabled
Here is also a PowerShell Script to disable Print spooler in domain PSBits/StopAndDisableDefaultSpoolers.ps1 at master · gtworek/PSBits (github.com)
This can also be done using Group Policy.
You should also enable PrintService/Operational log for servers that require Print Spooler running for the time being.

If you have Microsoft Defender for Identity, you will also get an alert if you have Print Spooler running on Domain Controllers, you can read more about the security recommendation here –> Microsoft Defender for Identity Print spooler identity security posture assessments | Microsoft Docs
For Citrix/RDS/VMware Horizon environments
If you are using 3.party print tools with their own unified print driver is still relies on the native print spooler service and is therefore still vulnerable to this attack. This applies to like ThinPrint, Tricerat, and other native 3.party print solutions.
Azure Log Analytics / Sentinel detection
If you want to collect and look after events from within Azure Sentinel / Log Analytics you need to collect the specific event log using data collection rules and collect from two custom log sources.
Microsoft-Windows-PrintService/Admin
Microsoft-Windows-SmbClient/Security

Then you can filter after EventId 808 (Microsoft-Windows-PrintService/Admin) , EventID 316 (Microsoft-Windows-PrintService/Admin) and 31017 (Microsoft-Windows-SmbClient/Security) when using Kusto Rules.
Event | where EventID == 808 | where EventID == 31017 | where EventID == 316

You can use the following Kusto Query via Microsoft Defender to determine if there has been modifications to the Print driver folder 2021-1675 – PrintNightmare KQL – MDE (github.com)
3. Party detection
Qualys customers can scan their network with QID 91772 to detect vulnerable assets with Qualys vulnerability manager.
Fortinet IPS Module also scans for this vulnerability –> Threat Signal Report | FortiGuard
What about Universal Print?
So far it seems that this vulnerability does not affect session which are using Universal Print from Microsoft.