After I’ve been dabling on a solution to try to fix a SSO solution between SAML and Citrix, I’ve been pretty much banging my head to the wall after trying out a bunch of different solutions. Then out of nowhere comes this along!
Yay! Finally an solution to what I have been trying to do for some time! So let’s deep-dive into it. I’m also going to use my own deployment as an example to show how this actually works. Note that this only works for Web receiver and not for native receiver setup. Now this example which was just for demonstrations I used a NetScaler SAML iDP setup in another site. Which was then setup using AD trust in the backend to make it simple. Now when a user tries to logon the NetScaler Gateway vServer it will be redirected to SAML iDP based upon the SAML authetication policy. The iDP vServer has a policy which triggers an AD auth policy and allows for LDAP authenticaiton against the remote Active Directory.
After auth is successfull the SAML assertion is returned to the NetScaler Gateway which then will take the token and apply the session policy and do SSO to Storefront. Storefront is configured only with NetScaler Gateway pass-trough setup and will then see the SAML assertion as a form of Smart Card. Because of the User Credential Service, Storefront is able to map the SAML identity assertion to convert that into a network virtual smart card logon for active directory.
So this solution is highly dependant on use of a Active Directory Certificate Services deployment interally, and using NetScaler for SAML iDP as well requires alot of certs to setup.
So just go trough a quick setup of this. (Note I have a wildcard certificate which handles the signing of the SP and for the aaa vServer)
1: NetScaler SAML iDP policy on the (samlidp.test.local) Note that the nsgw2.test.local is my NetScaler Gateway vServer which acts as an SAML SP.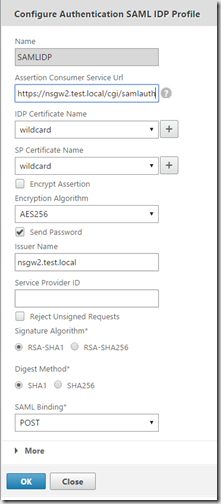
Then I have an policy expression which looks like this, which means that if traffic which contains the URL (saml) it should trigger the samlIDP policy which has the action SAMLIDP.
I also have an LDAP policy bound to this SAML iDP vServer which has the expression of ns_true, because I want to have the SAMLIDP do LDAP based auth backend and then return an SAML assertion to the SAML SP (Which is NetScaler Gateway)
The SAML Policy on the Gateway vServer
Then we just need a regular Session Policy which does the SSO to web applications and add the Storefront Web Receiver URL as well.
In my case I installed both of these components on my StoreFront server.
the other MSI components needs to be installed on the VDA (Requires 7.8!!!) Also you need to configure the domain controllers to have ready for smart card authentication (Which is described here –> http://support.citrix.com/article/CTX206156 )
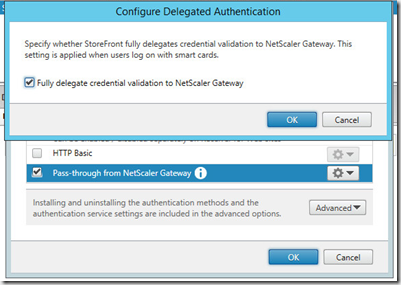
Configure that password validation should be done on the NetScaler gateway, and define the Store for Passtrough via NetScaler Gateway.
After installing this on the Storefront server you need to get a policy ADMX file from the installed and place in on your central store repository, it can be found here –>
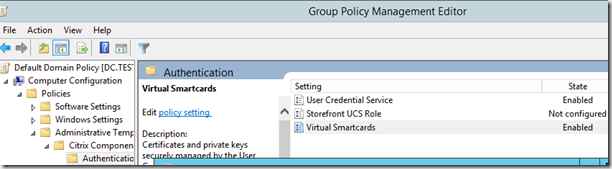
Then after setup open GP manager and change the default domain policy (It is only needed for Storefront and VDA agents which need to see the UCS DNS server)
Configure the User Credential Service and Virtual Smartcards setting. Note under User Credential Service you need to specify the DNS server of the server that runs the UCS service! In my case it is the StoreFront server.
After that you need to run an GPupdate before you continue the process. Next you need to run the Citrix User Credential
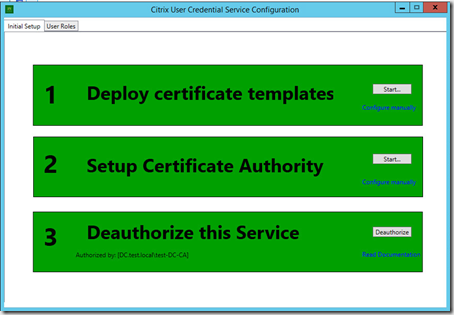
I have already done the steps (hence the green color) but what it does is basically publish some certificate templates to the AD CS (PKI enviroment) but on the third task you need to go to the AD CS and click Issue certificate (Since the USC service will ask for a certificate from the CA)
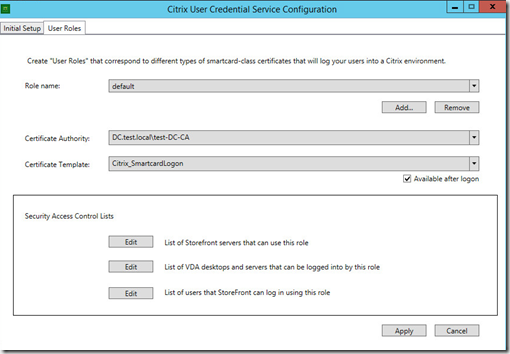
After this is done all 3 parts will have a green light, if we go into roles we can adjust which storefront servers and users / vda
So the traffic flow will look like this.
1: Users goes to NSGW
2: NSGW SAML Policy redirects logon to SAMLiDP
3: User enters username & password, SAMLiDP has AD auth
4: Successfull login the SAMLiDP redirects SAML assertion to SAMLSP which is the NSGW
5: NSGW forwards to SAML Assertion to Storefront
6: Storefront takes the SAML Assertion and generates an communicates with the USC service
7: UCS service generates a user cert from the CA
8: Storefront presents the cert to the VDA agent
9: Good to go!
However there are some gotchas you need to be aware of as of now.
BUG0606299 — When logging in to a Windows Server (2012 R2) VDA, the “Smart card service” must be running on the client machine.
BUG0608266 — Non-Windows Receiver clients cannot log into a Windows Server (2012 R2) VDA.
BUG0606512 — StoreFront requires that users have an explicit userPrincipalName name attribute set in Active Directory to use the User Credential Service.
BUG0612372 — UCS needs to create inbound firewall rule to allow connections during installation.
BUG0610430 — UCS logon occasionally gets stuck during logon process Welcome screen after authentication is completed.