A change of subject for my matter, but security has always been a huge interest of mine.
However, I thought that I would write about phishing attacks.
Now the art of phishing is just about trying to fetch information from people (and in there useful information such as social ID, bank card information and or username & password)
Think of the hacker as the fisherman and the user as the innocent fish just waiting to bite the lure. 
Web phishing is not a new phenomenon; it has been with us since the beginning of the nineties, but with the later years it has become more and more advanced and the hackers go to further lengths in order to get information from the user.
Now I had a friend that was looking to by some new dresses online, and she happened to come across this website.
http://www.777dress.org/
She was about to start buying some dresses but something seemed fishy about the website and asked if I could give it a quick look before she continued her shopping spree.

and as you see from the first page on the site there are multiple focus areas that draws people’s attention.
1: “Free Shipping” makes it more appealing to buy these clothes online since they don’t have to think about the shipping fee.
2: “70% sale off” people love to buy things on sale, why ? people are mostly greedy J
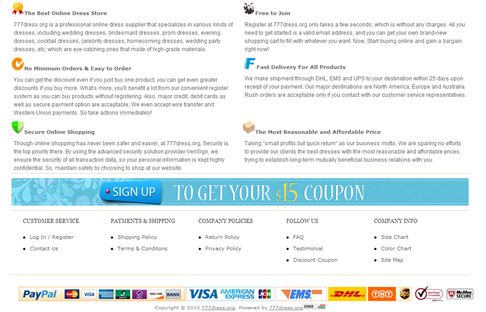
3: Logos from known paying solutions “MasterCard, VISA” gives the user false hope that the website is secure.
4: Buzzwords like “Secure, Free, Fast, Best” again to lure the user.
Now at the first glimse the website looks “good” enough. Many people that think about web frauds think that they would see a poorly written website with a bad setup but as I said earlier, the attacks have become more and more complex.
And therefore hackers spend more time on making their websites look authentic.
And when we choose something we want to add to the cart, we also get a logo of PayPal to ensure the user of the security

And when we proceed with the login and sign-up of a new account on the web site it never switches to https so the signup and sign in process is never encrypted which most web shops have.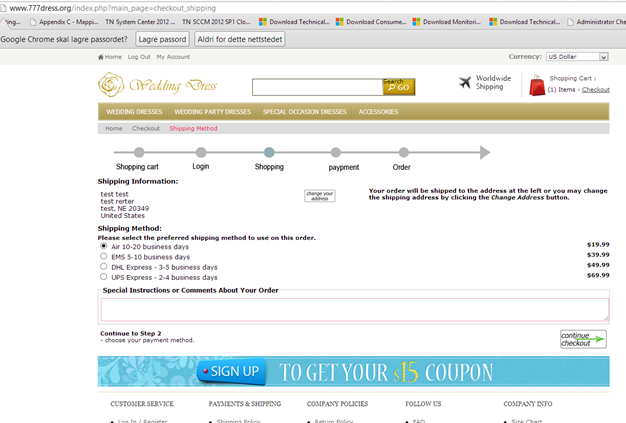
So lets proceed,
I also received an e-mail from a gmail account when I registered with the site. 
Interesting that they have actually created a google plus account for the user as well, lets figure out more J

Looks like they have created a fake profile with a fake picture as well, when I do an image search on google on the same picture I get numerous hits on the same picture used in loads of different online e-shops.
For instance (Which is much of the same web shop design as the other one)
http://www.weredress.net/
So let’s continue with the order on the previous site.

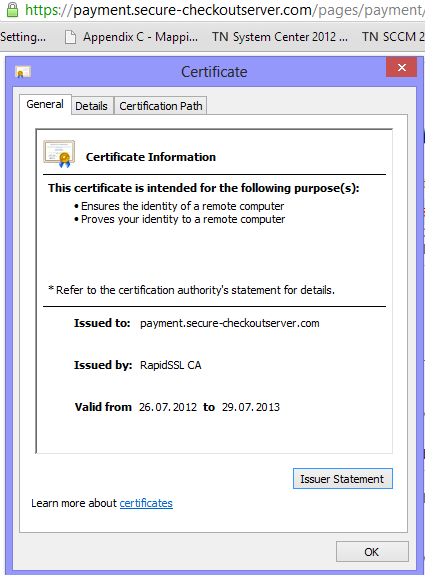
Next I receive an email that the order is complete and I am redirected to a VISA web site where I am to enter my information

And if you look at the URL there is an valid certificate there as well.
What happens if we enter some bogus information?

What no support for my bogus card ? L
This is also another trick, since it might happen that I try multiple cards since there is not support supposedly for the first card J
In the background there are some intelligent javascripts that are running and collects all the information that you are typing in.
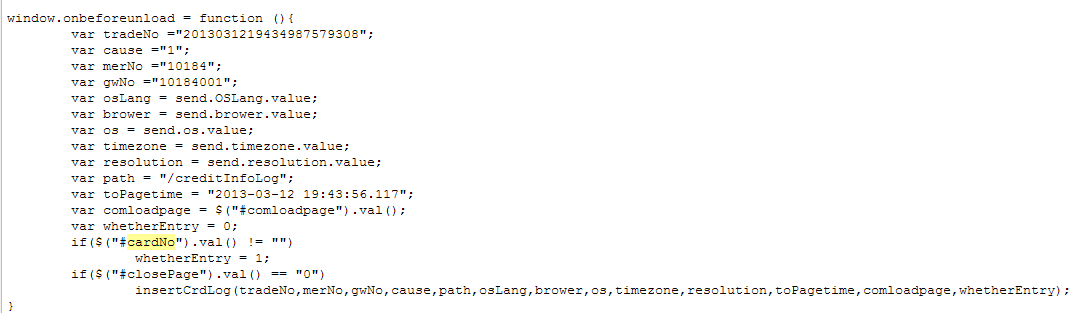
This one collects a lot of information regarding your clients and os.
But what happens if I press Cancel on the process?

wow! Didn’t even have to pay for the dress now that’s good business. J
Now other things we can look at to find out more about 777dress.org
We can also see that the authoritative DNS server for the site is located in China

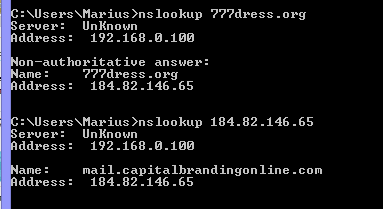
If we run an nslookup we can see that it shares IP with another site.
mail.captialbrandinonline.com ? that sounds fishy.

They apparently haven’t finished building their websites yet… L
And if I run a whois on the domain 777dress.org I get a lot of bogus information.

Apparently, I looks to origin from China, with no apparent information to where it is located.
A quick nmap scan shows OpenSSH, WebServer and MySQL port open (tisk tisk..)

Just for information OpenSSH 4.3 was released in 2006 and can be exploited.
And I did a similar scan on the other site mail.capitalbrandingonline.com and found numerous ports and older services that could be exploited.
So in the end I think that we concluded with that this site is a scam.
Things to look for:
1: Look at the written language of the websites (Often there is poorly written language on web scams)
2: When you login and sign-up remember to look after an encrypted login and that you don’t receive e-mail from a gmail / Hotmail / yahoo etc)
ß This padlock ensures that all communication is encrypted.
3: To many logoes from known payment companies on the front page (This is mostly to give the user fake sense of security )
4: Do a whois on the domain, you can see for instance in my case that the domain was created in 2012 and had bogus information. You can do a whois here à
http://whois.net
5: Gives you an “approval” e-mail, most websites have an approval function that sends an e-mail to the email account that was entered in the account info page that makes sense, this site however did not.
6: Google the site! In many cases you can see others written of forums about the site and have fallen into the trap.
7: Use the force. Use some common sense in the matter J and follow the points above before entering ANY sensitive information to a website you have never been on before.
