Earlier today (16th of April) FHI together with Simula launched their new app SmitteStopp (referenced here –> https://helsenorge.no/smittestopp#Slik-virker-appen) here you can read more about how the application functions and also what kind of data it collects. Now I was curious how this was setup on the backend which is running in Microsoft Azure so I decided to do a bit digging, since this service was setup in Azure and also something I’m skeptical about.
Now I know that there has been a team of experts involved into evaluating the security of the applications and the service in general, but I’m still a bit skeptical about how much they looked and evaluated the backend design and services.
NOTE: I collected data from my DNS logs and together with public information that was available here –> https://www.fhi.no/contentassets/72bffef9f021424d965d93866a82f930/dpia-smittestopp.pdf which gave some insight into what was being used in the backed. Also some of this is speculation since I do not have access to the backend resources.
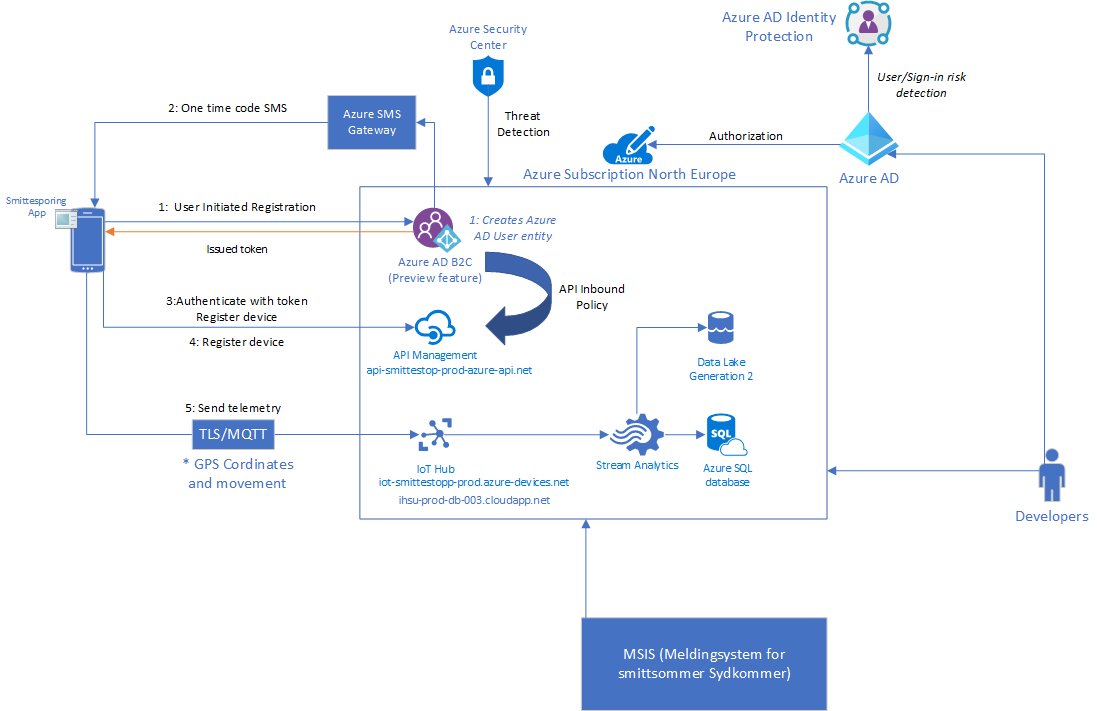
First of Smittestopp is running on the Azure datacenters in Ireland. Why not Norway or West Europe?
The application and service is using a set of different features which as of now is not available in the Azure Norwegian datacenter. such as one of the features is the IoT Hub, you can view the services availability here –> (https://azure.microsoft.com/en-us/global-infrastructure/services/?regions=norway-east,norway-west,europe-west,europe-north&products=all) so in order to collect the data and process it in the same location the went with North Europe.
Now why not West Europe? This can be a deliberate choice but! the last couple of weeks, West Europe has had capacity issues and Microsoft has put restrictions on it compared to other (https://telecoms.com/503376/microsoft-places-restrictions-on-azure-as-demand-increases-by-775/) . So North Europe is the logical choice.
Another feature that this service is using is a feature from Microsoft called Azure AD B2C with a Phone based authentication method. This is the mechanism which allows you to register your device using just your phone number. Essentially this service (https://docs.microsoft.com/en-us/azure/active-directory-b2c/phone-authentication)
NOTE: A lot of different people are saying that they get SMS from different vendors and this is true, because Microsoft uses a range of different vendors to send SMS trough their gateway service.

Once you have signed up, the device is authorized and will start to transmit data using MQTT v3.1.1 on port 8883 over TLS to the IoT Hub. Which is then processed somehow (I’m guessing Stream Analytics) into Data lake gen 2 and SQL Database.
You can view a bigger example of the picture here –> https://twitter.com/msandbu/status/1250900953160724481/photo/1
Now many have had issues completing this sign-up part here with getting an SMS and signing up, one reason for that the Azure AD B2C Phone registration feature is in preview from Microsoft, and when Microsoft has a feature in preview in Azure it means that there is no guaranteed SLA, secondly the scale of the service might not be as it would be when it hits general availability.
So far in addition to some of the security services that has been mentioned it gives me this overview picture which is shown above. Now looking at the setup there are a couple of things that I will raise a red flag, since I don’t have the insight on the backend this is purely speculations, but I’ve seen this so many times before in other enviroments.
- Using services in public preview is not something that should be used as part of this application that is being rolled out. And also since Microsoft uses multiple vendors to send SMS trough their services, the application should give a bit better indication about where the SMS might come from.
- How is access to the backend actually secured? One thing that is mentioned is that the development is secured using Identity Protection, but this only applies to user-risk and sign-in risk. What if a legitimate user on the inside goes and download data directly from the SQL Database or the Data Lake? will this trigger an activity alert?
- How is the data encrypted in Azure SQL is it use TDE? Encryption at rest is one thing, but ensuring that people that has access to the enviroment can view the live data is another.
- They also mention that they use Security Center, but default settings in Security Center does not look into PaaS services which is the main services used here, secondly it looks at abnormal activity and threat detection, what if a developer suddenly sets up a new service with a public endpoint? are there Azure policies and proper RBAC in place to ensure that this does not happen?
- What kind of IAM processes are in place to ensure that only certain people have access and only have access to what is needed?
I have seen my fair share of bad configuration and using default settings, so I hope that Simula and FHI have taken serious consideration on how the backend is configured to ensure proper access control, logging and monitoring and encryption of data.