Yeah, I’ve been silent for a while but that is because I have been attending a training course on NSX this week, and ohh boy it has been a great learning experience.
The first real reason why I wanted to attend the NSX training course was because of the microsegmentation capabilities, but as I quickly understood this was only a small portion of the feature set that is available in the product.
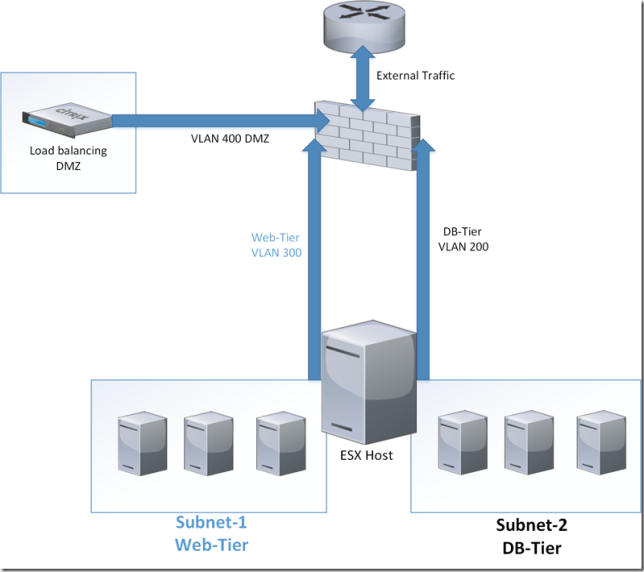
So why is it so cool? firstly lets look at an tradisional network setup using firewalls, routers, switches and so on. We have our different VLANs configured on each of the switches and on the VDS. We have our firewall further up the chain which is checking all the traffic going back and forth between the different zones, this might just as well be ACLs on the switches. This is a simple drawning of something that is of course much more complex in a datacenter enviroment
Let us say that we have an e-commerece website which consists of a two tier setup, an web-tier and DB-tier. Which are placed on different subnets. External traffic is going via the external load balancing which load balances between the different web-servers. When there is a query from the web-servers they will go back across the wire, back to the firewall and then to the other subnet which is the DB-tier. Which is this case means that traffic going between two virtual machines on the same host needs to go out the wire, be processed by the firewall then back to the same host to another virtual machine. Whcih generates alot of north-south traffic, also this isn’t really scaleable for the firewall, since in many cases is a large box with alot of troughput which has to process everything for each VLAN/Subnet.
So how would this look like in a NSX enviroment?
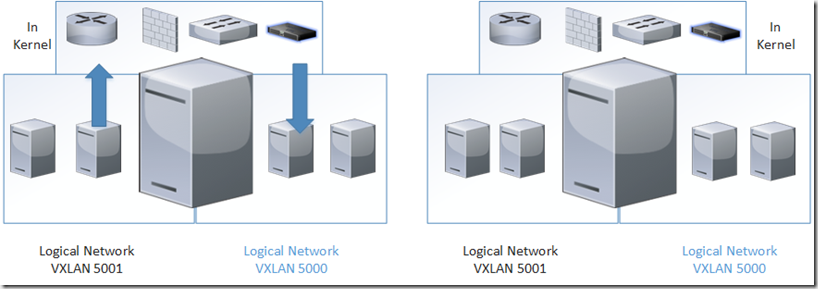
Well to sum it up, NSX consists of different modules, such as Distributed Logical Router (Which is an in-kernel modul) what this does, is at allows for in-kernel routing between logical networks (running VXLAN) so for instance, for virtual machines that need to communicate between Logical Network 5000 and 5001 that might be processed on the SAME ESX Host, meaning that the traffic does not need to out to the physical networks.
Same goes for firewall, which also is a distributed firewall on each ESX host, rules are processed before a virtual machine is allowed to send a traffic and before it is received to another virtual machine on the same esx host. Using VXLAN we can also stretch L2 across different networks, without doing much on the physical network (No VLAN configuration required) which in essence we can have a flat l2 network. Distributed load balancing is also a feature which is coming later, but as we can see more and more features which has earlier been a dedicated appliance can now be processed directly in the VMkernel, which also allows for pure scale out architecture.
NOTE: Load balancing is still in tech preview
Does it cost alot of money? Sure it does! but you have to think about what you are actually saving here in terms of overhead.
- Routing traffic going north/south handeld by the DLR which might be on the same host.
- Spanning L2 traffic over L3 network, without having to define “anything” on the switches in term of VLANs, when for instance moving a VM using vMotion to another location.
- Distributed firewall which scales with each ESX host and all policies are handled by each ESX host before entering and leaving the host. (Aka Microsegmentation)
- Load balancing using HAproxy
- SSL VPN and L2VPN
- Security composer which allow us to create security group and security policies which can be trigged based upon different criteria and moving objects to different groups.
- REST API to automate anything!
- Integrate with thirdparty vendors to get access to features like IDS/IPS, Antivirus, DLP, vurnleability scan, more advanced capabilities.
And there is more to come!
Distributed load balancing within the kernel module is in preview –> https://communities.vmware.com/docs/DOC-30247
And also moving forward, VMware is expanding the NSX capabilities into different cloud providers as well
Which will in essence allow L2 networking across any cloud provider, managed from the same solution.