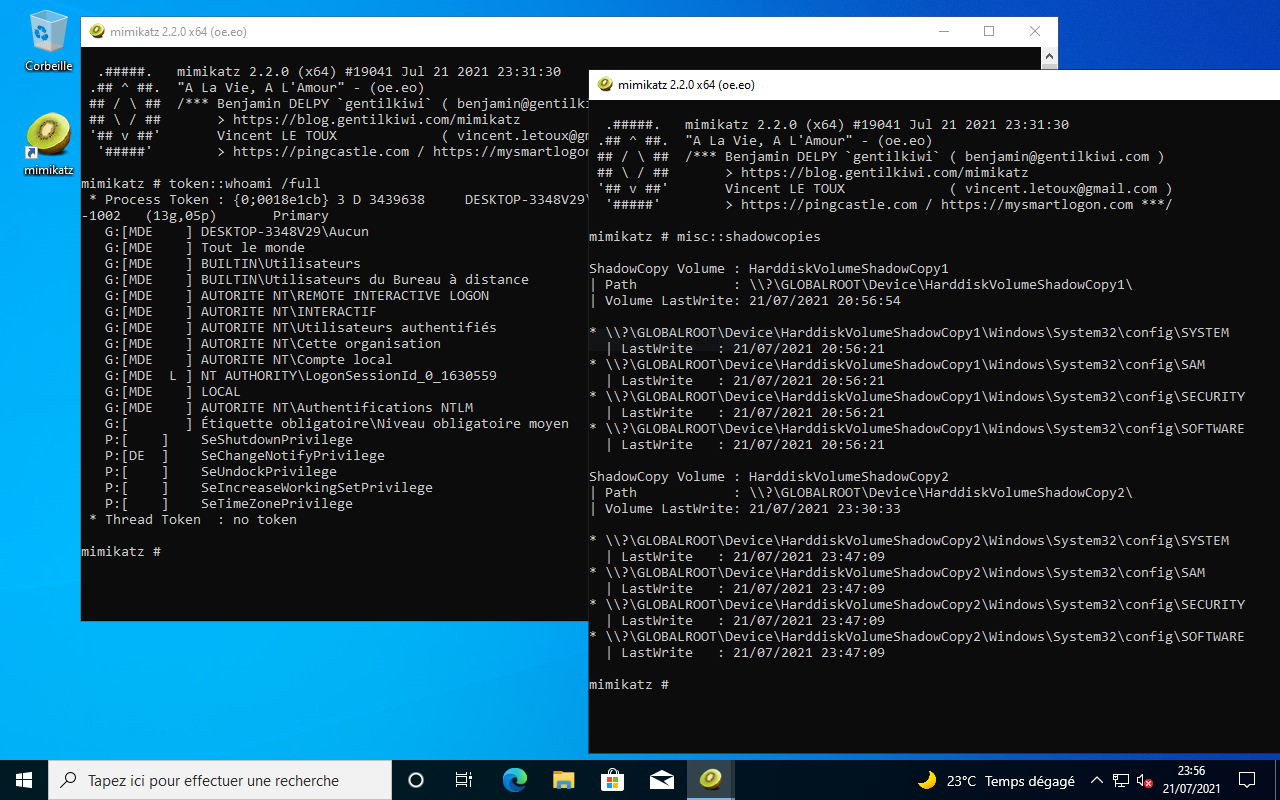
A couple of days ago a new vulnerability was found in Windows 10, where the SAM (Security Account Manager) database was readable for regular local users given that it could open the database from shadow copies.
This was found by (Jonas L (@jonasLyk) / Twitter)

And this only affects Windows 10 version 1809 and newer operating systems.
So how bad is this? well, an attacker who successfully exploits this vulnerability could run arbitrary code with SYSTEM privilege.
As of now there are now patches available for this, but Microsoft has created a vulnerability note and stated what can be done to fix this issue –> CVE-2021-36934 – Security Update Guide – Microsoft – Windows Elevation of Privilege Vulnerability
An exploit has also made available as part of Mimikatz.
It should be noted that by default VSS is not running
Workarounds
Restrict access to the contents of %windir%\system32\config
- Open Command Prompt or Windows PowerShell as an administrator.
- Run this command:
icacls %windir%\system32\config\*.* /inheritance:e
Delete Volume Shadow Copy Service (VSS) shadow copies
- Delete any System Restore points and Shadow volumes that existed prior to restricting access to %windir%\system32\config.
- Create a new System Restore point (if desired).
Impact of workaround Deleting shadow copies could impact restore operations, including the ability to restore data with third-party backup applications.
Note You must restrict access and delete shadow copies to prevent exploitation of this vulnerability.